The Canadian Privacy Law Blog: Developments in privacy law and writings of a Canadian privacy lawyer, containing information related to the Personal Information Protection and Electronic Documents Act (aka PIPEDA) and other Canadian and international laws.
Recent Posts
- This blog has moved
- Some thoughts on street photography
- RCMP changes rules for criminal records checks
- Saskatchewan amends privacy regs to permit solicia...
- US Federal judge declares warrantless wiretapping ...
- Commisser releases discussion paper on cloud compu...
- Heathrow worker given police warning for body scan...
- How Privacy Vanishes Online, a Bit at a Time
- Facebook plans to allow users to "share" location
- Drawing the curtain on ISP cooperation with law en...
On Twitter
About this page and the author
 The author of this blog,
David T.S. Fraser, is a Canadian privacy lawyer who practices with the
firm of McInnes Cooper. He is the author of the Physicians' Privacy Manual. He has a national and international practice advising corporations and individuals on matters related to Canadian privacy laws.
The author of this blog,
David T.S. Fraser, is a Canadian privacy lawyer who practices with the
firm of McInnes Cooper. He is the author of the Physicians' Privacy Manual. He has a national and international practice advising corporations and individuals on matters related to Canadian privacy laws.
For full contact information and a brief bio, please see David's profile.
Please note that I am only able to provide legal advice to clients. I am not able to provide free legal advice. Any unsolicited information sent to David Fraser cannot be considered to be solicitor-client privileged.
Privacy Calendar
Archives
- January 2004
- February 2004
- March 2004
- April 2004
- May 2004
- June 2004
- July 2004
- August 2004
- September 2004
- October 2004
- November 2004
- December 2004
- January 2005
- February 2005
- March 2005
- April 2005
- May 2005
- June 2005
- July 2005
- August 2005
- September 2005
- October 2005
- November 2005
- December 2005
- January 2006
- February 2006
- March 2006
- April 2006
- May 2006
- June 2006
- July 2006
- August 2006
- September 2006
- October 2006
- November 2006
- December 2006
- January 2007
- February 2007
- March 2007
- April 2007
- May 2007
- June 2007
- July 2007
- August 2007
- September 2007
- October 2007
- November 2007
- December 2007
- January 2008
- February 2008
- March 2008
- April 2008
- May 2008
- June 2008
- July 2008
- August 2008
- September 2008
- October 2008
- November 2008
- December 2008
- January 2009
- February 2009
- March 2009
- April 2009
- May 2009
- June 2009
- July 2009
- August 2009
- September 2009
- October 2009
- November 2009
- December 2009
- January 2010
- February 2010
- March 2010
- April 2010
Links


Blogs I Follow
Small Print
The views expressed herein are solely the author's and should not be attributed to his employer or clients. Any postings on legal issues are provided as a public service, and do not constitute solicitation or provision of legal advice. The author makes no claims, promises or guarantees about the accuracy, completeness, or adequacy of the information contained herein or linked to. Nothing herein should be used as a substitute for the advice of competent counsel.
This web site is presented for informational purposes only. These materials do not constitute legal advice and do not create a solicitor-client relationship between you and David T.S. Fraser. If you are seeking specific advice related to Canadian privacy law or PIPEDA, contact the author, David T.S. Fraser.
Friday, February 06, 2009
4th Annual Payment Card Compliance In Canada
I had the pleasure of speaking this morning at the Canadian Institutes 4th Annual Payment Card Compliance In Canada. I was on a panel with Art Dunfee, Director General of Investigations and Inquiries at the Office of the Privacy Commissioner of Canada and Sandy Stephens, Senior Manager, Legal CounselCapital One Canada. Sandy covered the new Do Not Call List and Art covered PIPEDA compliance and the new breach notification guidelines. I then presented on a few additional topics: (i) the effect of US breach notification laws on Canadian companies and (ii) the effect of provincial anti-USA PATRIOT Act laws on Canadian banks.
Here's my presetation if you're interested:
And if Google Documents isn't showing you the love, here it is as a PDF: Payment%20Card%20Compliance.pdf
Labels: breach notification, patriot act, piidpa, privacy
Tuesday, January 20, 2009
Heartland data breach could be bigger than TJX's
Heartland Payment Systems has announced that it suffered a significant data breach last year after it was discovered that hackers had installed software on their systems to capture credit card information. The firm apparenly processes over 100 Million tranactions a month, leading to speculation that this may dwarf the 2007 TJX breach. See: Heartland data breach could be bigger than TJX's.
Labels: breach notification, information breaches, privacy, tjx
Friday, October 10, 2008
Missing hard-drive in the UK contains info on 100K military personnel
Labels: breach notification, incident, privacy, uk
Monday, August 18, 2008
CBA urges Government to reform Privacy Act
News Release: Commissioner welcomes legal community’s call for privacy law reform (August 18, 2008) - Privacy Commissioner of CanadaCommissioner welcomes legal community’s call for privacy law reform
Quebec City, August 18, 2008 — A Canadian Bar Association (CBA) resolution once again highlights the urgent need for reform of Canada’s federal public sector privacy legislation, says the Privacy Commissioner of Canada, Jennifer Stoddart.
“With this resolution, lawyers from across the country are urging the government to strengthen privacy protection for Canadians. Canada’s federal sector privacy legislation, the Privacy Act, is unbelievably inadequate,” says Commissioner Stoddart. “I hope the federal government will heed the CBA’s call for modernization of the Act. This is the latest in a string of appeals from privacy experts about the need to update legislation which has been far outpaced by technological and societal changes.”
The CBA, which is holding its 2008 Legal Conference in Quebec City, passed the resolution calling for comprehensive revision of the Privacy Act on the weekend.
In particular, it proposes changes to the legislation to ensure that:
- Federal government departments only collect personal information when demonstrably necessary for clear and articulated state goals;
- Once collected, personal information is rigorously protected with stringent safeguards and accountability requirements, including a breach notification requirement; and
- Personal information is not shared within or beyond Canada’s borders unless those safeguards and requirements can be guaranteed.
The Office of the Privacy Commissioner of Canada (OPC) has long been advocating for reform of the Privacy Act, which is a quarter-century old and has never been substantially updated.
Last spring, the House of Commons Standing Committee on Access to Information, Privacy and Ethics began a study of the Privacy Act and possible amendments. The OPC reform proposals to the committee are posted at http://www.privcom.gc.ca/keyIssues/ki-qc/mc-ki-pa_e.asp. The OPC looks forward to the Committee’s recommendations.The CBA resolution is available at www.cba.org/cba/resolutions/pdf/08-06-a-pdf.pdf. The Privacy Commissioner of Canada is mandated by Parliament to act as an ombudsman, advocate and guardian of privacy and the protection of personal information rights of Canadians.
Labels: breach notification, privacy, privacy act
Wednesday, June 04, 2008
Privacy Commissioner tables annual PIPEDA report
The Privacy Commissioner of Canada tabled her annual report to Parliament on the Personal Information Protection and Electronic Documents Act for 2007 on June 3, 2008.
The report is here: Annual Report to Parliament 2007 Report on the Personal Information Protection and Electronic Documents Act - Privacy Commissioner of Canada.
Here is the accompanying media release:
Lack of basic privacy and security measures causing major data breaches, Privacy Commissioner saysTabling of Privacy Commissioner of Canada's 2007 Annual Report on the Personal Information Protection and Electronic Documents Act
Ottawa, June 3, 2008 — Too many data breaches are occurring because companies have ignored some of the most basic steps to protect personal information, says the Privacy Commissioner of Canada, Jennifer Stoddart.
The Commissioner’s 2007 Annual Report on the Personal Information Protection and Electronic Documents Act (PIPEDA) was tabled today in Parliament.
“Many companies need to do more to prevent inexcusable security breaches,” Commissioner Stoddart says. “Too often, we see personal information compromised because a company has failed to implement elementary security measures such as using encryption on laptops.”Voluntary privacy breach guidelines which the Office of the Privacy Commissioner (OPC) developed with business and consumer groups, and published last summer, appear to be prompting more organizations to report breaches.
The OPC has received 21 voluntary breach reports in the first five months of 2008. Last year, there were 34 voluntary reports of breaches to the OPC – up from a total of 20 reports in 2006.
Over the last few years, hundreds of thousands of Canadians have been affected by data breaches.
“Many organizations want to be good corporate citizens and do the right thing,” says Commissioner Stoddart. “While the increased number of reports is a positive sign, it’s clear we still aren’t hearing about every breach which could have a harmful impact on people.”
Financial institutions are reporting the largest number of breaches to the OPC. Some telecommunications, insurance and retail companies have also reported breaches.
The OPC is concerned that few small- and medium-sized enterprises are reporting breaches.
Examples of reported breaches include the theft of laptops containing unencrypted personal information, data tapes lost in transit, improperly discarded paper records, and misdirected faxes.
Information the OPC is collecting from the voluntary reports is helping to shed light on some of the common problems which are leading to breaches.
It is clear, for example, that unprotected laptops remain a huge issue which companies must address. Many breaches related to electronically stored data, often customer information stored on stolen laptop computers. Almost nine in 10 people whose data was compromised by a self-reported breach in 2007 were put at risk because their personal information was held in an electronic format that was either not secured or lacked adequate protection mechanisms such as firewalls and encryption.
Other breaches occurred because employees had not followed established company practices. Companies can address this problem by providing ongoing privacy training, yet a poll commissioned by the OPC last year found only a third of all businesses had trained staff about their responsibilities under Canada’s privacy laws.
The OPC strongly supports a plan by Industry Canada to introduce mandatory breach notification. Reporting requirements will encourage businesses to do more to reduce the risk of a data breach and ensure all organizations are playing by the same rules. They will also ensure Canadians are notified about serious breaches.
Industry Canada has prepared draft breach notification reporting rules and is now fine-tuning this model based on stakeholder input.
The current proposals suggest the federal government is generally headed in the right direction and that Canada will have a breach reporting regime which is both reasonable and flexible.
As the federal government completes its work on reporting requirements, the OPC continues to investigate a wide range of privacy complaints.
The OPC received 350 new PIPEDA complaints during 2007. Almost one third of complaints involved financial institutions. As in past years, other major sectors for complaints were telecommunications, insurance, sales and transportation. The annual report is available on the OPC website.
The Privacy Commissioner of Canada is mandated by Parliament to act as an ombudsman, advocate and guardian of privacy and the protection of personal information rights of Canadians.
To view the report:
Annual Report to Parliament 2007 — Report on the Personal Information Protection and Electronic Documents Act (Adobe format)
Labels: breach notification, laptop, privacy
Friday, May 09, 2008
Ontario and B.C. Privacy Commissioners issue joint message: personal health information can be disclosed in emergencies and other urgent circumstances
This just crossed the wires and is likely of interest to those who followed the earlier discussions about using privacy legislation as an excuse for inaction.
CNW Group OFFICE OF THE INFORMATION AND PRIVACY COMMISSIONER/ONTARIO Ontario and B.C. Privacy Commissioners issue joint message: personal health information can be disclosed in emergencies and other urgent circumstancesOntario and B.C. Privacy Commissioners issue joint message: personal health information can be disclosed in emergencies and other urgent circumstances
TORONTO, May 9 /CNW/ - In light of recent events, such as the tragic suicide of Nadia Kajouji, a student at Carlton University, and the Virginia Tech massacre of 2007, the Information and Privacy Commissioner of Ontario, Dr. Ann Cavoukian, and the Information and Privacy Commissioner of British Columbia, David Loukidelis, are reaching out to educational institutions, students, parents, mental health counsellors and healthcare workers in both provinces: personal health information may, in fact, be disclosed in emergencies and other urgent circumstances. The two Commissioners want to ensure that people realize that privacy laws are not to blame because they do permit disclosure.
The Commissioners want to send the clear message that privacy laws do not prevent counsellors or healthcare providers from contacting a person's family if there are real concerns that they may seriously hurt themselves. "When there is a significant risk of serious bodily harm, such as suicide, privacy laws in Ontario clearly permit the disclosure of personal information without consent, regardless of age. In such situations, schools may contact parents or others if there are reasonable grounds to believe that it is necessary to do so," says Commissioner Cavoukian. Commissioner Loukidelis adds that, "If there are compelling circumstances affecting health or safety, or if an individual is ill, B.C.'s privacy laws allow disclosure to next of kin and others, including school officials and health care providers. Individual cases can be fuzzy, but if someone uses common sense and in good faith discloses information, my office is not going to come down on them. Privacy is important, but preserving life is more important."
In Ontario, the Personal Health Information Protection Act (PHIPA) allows health care providers, such as mental health counsellors, to disclose personal health information when necessary to eliminate or reduce a significant risk of serious bodily harm. This would include disclosure to a physician or parent if there are reasonable grounds to believe it is necessary to do so. In fact, PHIPA specifically allows for this kind of disclosure in emergency or urgent situations. Commissioner Cavoukian clarified this in a Fact Sheet she issued in 2005 entitled, Disclosure of Information Permitted in Emergency or other Urgent Circumstances, available at http://www.ipc.on.ca/.
In British Columbia, Commissioner Loukidelis underscored, the public sector Freedom of Information and Protection of Privacy Act allows universities, schools, hospitals and other public institutions to disclose personal information where someone's health or safety is at risk. He also noted that the private sector Personal Information Protection Act contains similar authority to disclose personal information for health and safety reasons.
Both Commissioners are today announcing their joint project to issue a new publication aimed at clarifying the role that privacy laws play when workers are trying to decide whether they can disclose personal health information. Commissioner Cavoukian said of the joint project, "Our goal is to ensure that educational institutions understand the legislative framework in advance of problems occurring. We are looking forward to working further with the educational community - stay tuned."
Commissioners Cavoukian and Loukidelis are urging those responsible for the health and safety of others to educate themselves about how the privacy laws covering them apply to their work and familiarize themselves with the provisions allowing them to disclose personal health information in emergency situations. Commissioner Loukidelis says, "I know that frontline decisions have to be made quickly and sometimes the facts may not be as clear as you'd like. But there's no doubt that privacy laws support disclosures to protect health and safety." Commissioner Cavoukian agrees that privacy laws are not at fault. "To infer that privacy laws were responsible for someone's death is to completely misunderstand the role that privacy laws are designed to play. The tragedy here lies if you take a default position of non-disclosure and inaction," says Commissioner Cavoukian. She also adds that, "However, Commissioner Loukidelis and I both recognize that the decision to notify someone's family without their consent can be extremely difficult, requiring very sound judgment. We are also clear that notification cannot be done on a routine basis and that students need to feel reassured that their privacy will be protected when they seek counselling or other health care services."
Labels: bc, breach notification, health information, ontario, privacy
Saturday, April 26, 2008
Feds to leave disclosure of data security breaches to businesses: legislative plan
One thing that was relatively consistent in the submissions at PIPEDA's five year review was to follow in the footsteps of more than half the US states to require notification of security and privacy breaches. Canwest is reporting on leaked draft legislation which will surely disappoint many in the privacy community. In effect, there is no mandatory reporting. Businesses get to determine whether there is a "high risk of significant harm" and only then do they need to report the breach to consumers. Not reporting has no consequences. See: Feds to leave disclosure of data security breaches to businesses: legislative plan.
Labels: breach notification, pipeda review, privacy
Friday, April 18, 2008
Privacy Commissioner Concerned With Ticketmaster's Privacy Practices
Privacy Commissioner Concerned With Ticketmaster's Privacy Practices, Encourages Companies to Adopt High Privacy Standards Across OperationsOTTAWA, April 18, 2008 – Privacy Commissioner of Canada Jennifer Stoddart expressed concern with the information collection and privacy practices of a major online ticket vendor. However, following an investigation by her office and that of Alberta Commissioner Frank Work , the privacy practices of Ticketmaster Canada Limited have been brought up to standard.
However, she encourages companies to adopt the highest standard of privacy practices possible, regardless of where they do business.
“Online commerce continues to grow and customers worldwide expect companies to safeguard their personal information in the course of their business,” says Jennifer Stoddart. “It simply makes good business sense for companies to implement excellent privacy practices across their operations. It is also the law in Canada.”
The Commissioner launched an investigation into the information collection practices of Ticketmaster Canada Limited after a private citizen filed a complaint alleging that the company’s policies and practices on the collection, disclosure and use of customers’ personal information did not comply with the Personal Information Protection and Electronic Documents Act (PIPEDA).
The Information and Privacy Commissioner of Alberta, Frank Work, investigated a similar complaint into how Ticketmaster obtained consent to collect its customers’ personal information and released an investigation report late in 2007.
The investigation conducted by the Office of the Privacy Commissioner of Canada examined the issue of consent, but also investigated whether Ticketmaster followed the principles of access, openness and accountability found in PIPEDA.
“I am now satisfied with the measures Ticketmaster undertook to resolve the complaints that were brought to our attention,” says Jennifer Stoddart. “But I am very concerned that, seven years after PIPEDA was enacted, a major online company operating throughout Canada was found to be in violation of the legislation.”
The investigation of Ticketmaster Canada’s privacy practices was led by Assistant Commissioner Elizabeth Denham. It found that although the company had a privacy policy in place, this policy was long, complex and difficult for consumers to read.
The Assistant Commissioner also found that Ticketmaster’s online customers were required to consent to their personal information being used for marketing purposes as a condition of purchasing a ticket – a clear violation of PIPEDA.
Following the two investigations, Ticketmaster has revised its privacy practices to explicitly communicate what personal information is collected, with whom it is shared, and how it is used. The company has also adapted its online notification and call-centre telephone scripts so that customers are provided with a choice of whether to opt in to receive marketing material from Ticketmaster and event providers.
Furthermore, Ticketmaster in the United States has amended its privacy policy to make it more understandable and user-friendly for its customers. However, it did not implement any mechanism to provide customers the choice of opting in to receive marketing material, as it has done for its operations in Canada and the United Kingdom.
The Commissioner will bring this distinction to the attention of her colleagues at the US Federal Trade Commission. As well, she will continue to encourage companies with operations in Canada and elsewhere to adopt the highest standard of information protection practices possible to ensure compliance with Canadian privacy law.
To view the case summary and backgrounder:
Labels: alberta, breach notification, pipeda findings, privacy
Thursday, April 17, 2008
Incident: Ontario patient files found in dumpster
The Ontario Information and Privacy Commissioner is investigating after old medical records were found in a dumpster behind a coffee shop by a retiree. The affected patients will have to be notified as the information is subject to PHIPA, which contains Canada's only mandatory breach notification. See: TheSpec.com - Local - St. Joe's patient files found in dumpster.
Labels: breach notification, health information, incident, ontario, phipa, privacy
Tuesday, April 15, 2008
Austrialian Commissioner seeks comments on draft breach notification guidelines
Labels: australia, breach notification, privacy
Thursday, March 27, 2008
iOptOut
Michael Geist has been a critic of the legislation enabling the new Canadian "Do Not Call List", which specifically permits calls from polling companies, newspapers, political parties and others. So to enable users to opt out even more, Michael has developed a website that sends specific do not call requests to individual companies and organizations. Check it out:
iOptOut - Welcome to iOptOutWelcome to iOptOut
The Canadian government passed legislation in 2005 mandating the creation of a do-not-call registry. The registry is scheduled to take effect in mid-2008, yet many Canadians may be disappointed to learn about the exemption of a wide range of organizations (registered charities, business with prior relationships, political parties, survey companies, and newspapers). Under the law, exempted organizations are permitted to make unsolicited telephone calls despite the inclusion of the number in the do-not-call registry. However, organizations must remove numbers from their lists if specifically requested to do so. IOptOut takes advantage of this approach by allowing Canadians to create and manage a personal do-not-call list that begins where do-not-call legislation ends. Once you register, you'll be able to view a categorized list where you can opt-out of further contact from exempt organizations.
To do this we send an email notification to each organization on your behalf requesting that your name, email address and phone number(s) be removed from their active marketing lists.
Labels: breach notification, dncl, privacy, telemarketing
Monday, January 21, 2008
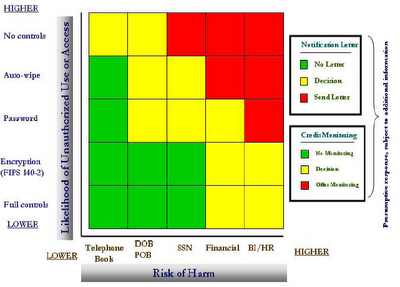
US Department of Commerce privacy incident response plan
Sabrina Pacifici has posted on her (fantastic) blog, beSpacific, a link to the privacy breach response plan put together by the US Department of Commerce: Department of Commerce Breach Notification Response Plan, September 28, 2007 (21 pages, PDF). This, in and of itself, is not particularly newsworthy but it's worth taking a look at as a precedent document in formulating such policies.
The document includes the Department's matrix for determining whether notification is required:
Labels: breach notification, privacy
Thursday, January 10, 2008
Security breach at the Canadian Bar Association
The Canadian Bar Association advises that it has noted "unauthorized activity" related to member information: CBA Personal Information Advisory.
Michael Geist quotes from the notification the CBA has sent to affected members:
Michael Geist - Canadian Bar Association Hit By Security BreachYour records may have been affected by this unauthorized activity. The files contained personal information relating to online orders (name, address, phone, fax, member number) and encrypted credit card information. We have no reason to believe that the encrypted credit card information was compromised. CBA uses one of the most secure encryption solutions available to protect credit card information. As a precautionary measure, we recommend that members monitor their credit card accounts for suspicious activity.
Labels: breach notification, incident, privacy
Friday, January 04, 2008
UK Committee calls for criminal penalties for data breaches
This is an interesting development. In response to the huge data breach in the UK (Canadian Privacy Law Blog: UK loses sensitive personal data on 25m people), the Parliamentary Justice committee is calling for criminal penalties for large data breaches. See: U.K. Needs Tougher Laws to Protect Private Data, Lawmakers Say - Bloomberg.com: U.K. & Ireland.
For some additional comments, see: IMPACT®: Data protection - more signs of unrest.
Labels: breach notification, europe, hmrc, privacy, uk
Friday, December 28, 2007
Privacy resolutions from the PCC
Privacy resolutions from the Privacy Commissioner of Canada:
News Release: Do you resolve to protect your privacy in 2008? (December 27, 2007) - Privacy Commissioner of CanadaDo you resolve to protect your privacy in 2008?
OTTAWA, December 27, 2007 – Threats to the privacy rights of Canadians will intensify in 2008 unless organizations resolve to do more to protect personal information, warns Privacy Commissioner of Canada Jennifer Stoddart.
“Heightened national security concerns, the growing business appetite for personal information and technological advances are all potent – and growing – threats to privacy rights,” says Commissioner Stoddart.
“The coming year will be another challenging one for privacy in Canada.”
With that prediction in mind, Commissioner Stoddart today released her 2008 list of top 10 suggested New Year’s resolutions for businesses, individuals and government.
Resolutions for businesses in Canada:
1. Protect personal information with strong security.
More than 162 million records were compromised by theft or loss in 2007, triple the number of data losses for the previous year, according to a USA Today analysis of breaches in the US, Canada and other countries. This alarming trend can be reversed if businesses begin to recognize the value of personal information. The disastrous breach involving Winner’s and HomeSense stores is an example of what can go wrong if businesses don’t invest in the latest security.
2. Use encryption to protect personal information on mobile devices such as laptops.
We are seeing too many headlines about personal information at risk because a laptop has been lost or stolen. Organizations must ensure personal information on a mobile device is encrypted – protecting information stored on a laptop with a password is simply not enough.
3. Ensure credit card processing equipment masks complete card numbers on receipts.
Complete credit card numbers should not be printed on receipts for electronically processed transactions. Businesses were supposed to switch to electronic processing equipment that masks card numbers – for example, by printing Xes – by the end of 2007. Printing complete card numbers exposes customers to the risk of identity theft. (Some very small businesses may still be manually taking imprints of cards because it is not economically feasible for them to purchase electronic equipment. They should still take all steps necessary to protect the information they collect.)
Resolutions for Canadians:
4. Think twice before posting personal information on social networking sites.
Many Facebook and Myspace users think of these sites as private, when, in reality, the information they post can often be seen by just about anyone. Before posting something, ask questions such as: How would I feel defending this comment or photo during a job interview five years from now? Am I harming someone else or invading someone’s privacy by posting this comment, photo or video? We like this simple rule of thumb: If Grandma shouldn't know, it shouldn't be posted.
5. Ask questions when someone asks for personal information.
It’s a good idea to understand why information such as your phone number or postal code, or driver’s licence is being requested and how it will be used. If you are concerned about receiving junk mail or telemarketing calls, decline to provide the information. Canada’s privacy laws offer you a choice about providing personal information that is not necessary for a transaction.
6. Take steps to protect your personal information.
Invest in a good shredder or burn all documents that include your name, address, SIN, financial information or other sensitive personal information. Papers containing personal information don’t belong in the recycling bin.
Resolutions for the federal government:
7. Overhaul the no-fly list to ensure strong privacy protections for Canadians.
The no-fly list involves the secretive use of personal information in a way that has very serious impact on privacy and other human rights. Innocent Canadians face the very real risk they will be stopped from flying because they’ve been incorrectly listed or share the name of someone on the list.
8. Move forward with proposed reforms to Canada’s privacy laws.
The federal government is currently holding consultations on important amendments to the Personal Information Protection and Electronic Documents Act (PIPEDA). These proposed changes include mandatory breach notification, a step that would encourage businesses to take security more seriously and protect Canadians against identity theft.
We also urge the federal government to open a review of the Privacy Act, which will be celebrating its 25th anniversary in 2008. Canadians should be offered the same level of legal protection under the Privacy Act as they have, as consumers, under PIPEDA.
9. Ensure that identity theft legislation is swiftly passed.
The government has introduced Criminal Code amendments to help police stop identity thieves or fraudsters before Canadians suffer actual financial harm. The changes include explicit penalties for collecting, possessing and trafficking in personal information.
10. Develop anti-spam legislation.
Canada remains the only G-8 country without anti-spam legislation, raising the danger that we will become a harbour for spammers. Halting the proliferation of spam is another important measure necessary to address identity theft.
The Privacy Commissioner of Canada is mandated by Parliament to act as an ombudsman, advocate and guardian of privacy and the protection of personal information rights of Canadians.
Labels: breach notification, facebook, laptop, privacy, privacy act, social networking, telemarketing
Wednesday, November 28, 2007
Reckless corporations may violate ID theft law
Fellow blogger David Canton is quoted in this interesting article that suggests reckless corporations may find themselves guilty of violating the new ID theft law:
Reckless Data Handling Could Violate ID Theft Law - Security Feed - News - CSO MagazineNov 27, 2007
Reckless Data Handling Could Violate ID Theft Law
The recently proposed amendment to the Criminal Code that would make "reckless" handling of personal information a crime can be troubling given the broad definition of the word, said one lawyer.
If Bill C-27 is passed, it will be an offense to make available or sell personal information (such as names, addresses bank account information and social insurance numbers) knowing it will be used to commit fraud -- or if the person or company selling the information is reckless as to whether the data will be used for fraud by a third party.
Bill C-27, an Act to Amend the Criminal Code (identity theft and related misconduct) was tabled in the House of Commons last week and passed first reading.
As reported by ITWorld Canada, vendors say Feds should enforce data encryption
The problem with measuring recklessness is a valid concern for organizations whose business relies on collecting customer personal information given the lack of industry standards, said Howard Simkevitz, lawyer with Toronto, Ont.-based law firm Lang Michener LLP.
Some international standards, from bodies such as the International Standards Organization (ISO), handle security compliance, but there is no equivalent for privacy, Simkevitz said.
"When we’re talking about identity theft and it’s the theft of personal information, that’s a distinct privacy-oriented term."
He added the term reckless includes the absence of precautions around securing customer personal data, so organizations should implement policies and procedures based around this. Overall, such precautions are mainly based on common sense and good corporate values around how to handle another person’s sensitive data, he said.
The privacy commissioner, he added, also makes available helpful guidelines around policies.
Actually, the Personal Information Protection and Electronic Documents Act (PIPEDA) provides a good starting point, he said, by advising organizations to determine whether the information they are collecting is personal, and if it is, to figure out if they have received consent to collect and use it for certain purposes.
"The risk of running afoul is at least minimalized, but there are tons of issues here, and the fact that now there are criminal sanctions that could be applied, is an issue," said Simkevitz.
The recklessness aspect of the bill is probably intended to capture people who do more than just act negligently, but "turn a blind eye" to securing personal information, said David Canton, a lawyer with London, Ont.-based law firm Harrison Pensa LLP.
When transferring that type of data to a third party, the organization should seek assurances that the recipient of the information is going to do what it has said it will do with the data, he said. Often, having contractual provisions to limit use of the data by a third party is useful, he added.
If companies seek such assurances, he said, "I would suspect that they haven’t crossed the reckless threshold."
But a rogue employee stealing customer personal information for the purposes of fraud could, depending on the circumstance, mean the company has been reckless, said Simkevitz. However, he said, if the company can demonstrate it took necessary actions to mitigate such risk, then it may not be held liable.
Typically, organizations are "vicariously liable" for actions of their employees, said Canton. Specifically, if the act committed falls within the ambit of that person’s job, then the organization can be held liable, he added, but "it’s not always an easy line to draw."
But given that Bill C-27 complements PIPEDA and other existing privacy legislation, said Canton, companies who have already dealt with privacy probably have dealt with the issues that this new bill presents.
The bill’s proposals do not add anything to existing legislation, said Canton, "but raises the bar and is maybe one way of putting criminal teeth in the security aspect of [PIPEDA], although it’s probably not its prime intention."
Canton said it’s hard to argue against some of the contents of the bill and it’s usually difficult to tell if such things will help deter identity theft, but it’s nonetheless a useful tool.
If anything, said Simkevitz, the bill "sensitizes corporations to the importance of protecting personal information."
In particular, he said, it’s great that it includes compensating victims of identity fraud, but it doesn’t address the issue of quantifying damages like the loss of a driver’s license versus hassle at the border because of issues with stolen identity.
"It certainly does [add teeth to PIPEDA]. Is this sufficient? I would be more reluctant to say that it is," said Simkevitz.
Besides that, he said the proposed amendment doesn’t address the use of spam to collect personal information, nor the issue of breach notification.
Labels: breach notification, privacy
Saturday, November 10, 2007
PIPEDA consultation marches onward
In case you haven't been consulted enough ...
The Government of Canada issued its response to the PIPEDA review report from the Standing Commitee on Access to Information, Privacy and Ethics, agreeing in parts and disagreeing in others with the committee's recommendations. So the government is now seeking public input on the topics that were relatively well canvassed before the parliaentary commitee.
If you have additional thoughts, you have until January 15 to make them known to Industry Canada.
Canada GazetteDEPARTMENT OF INDUSTRY
IMPLEMENTATION OF THE GOVERNMENT RESPONSE TO THE FOURTH REPORT OF THE STANDING COMMITTEE ON ACCESS TO INFORMATION, PRIVACY AND ETHICS ON THE PERSONAL INFORMATION PROTECTION AND ELECTRONIC DOCUMENTS ACT
Deadline for submission of views: January 15, 2008
On October 17, 2007, the Government of Canada tabled in Parliament its response to the Fourth Report of the Standing Committee on Access to Information, Privacy and Ethics (ETHI) on the statutory review of the Personal Information Protection and Electronic Documents Act (PIPEDA). In support of the Minister of Industry's responsibility for PIPEDA, Industry Canada is seeking the views of Canadians on a number of issues related to the response, including proposals for legislative amendments to PIPEDA.
PIPEDA, which came into force on January 1, 2001, sets rules for the collection, use and disclosure of personal information in the course of commercial activity in Canada. In a modern, information-based economy, an effective and efficient model for the protection of personal information is vitally important to ensure that the privacy of Canadian consumers remains protected. The ETHI Report contains 25 recommendations for how PIPEDA could be fine-tuned to ensure that the Act continues to achieve this objective. The government response expresses agreement with a majority of the Committee's recommendations and reflects the view held by a number of stakeholders that PIPEDA is working well and is not in need of dramatic change at this time. However, a small number of specific amendments may be warranted, and this consultation process provides Canadians with the opportunity to present further information, advice and views regarding the implementation of key proposals for legislative change.
In particular, Industry Canada is seeking views on the implementation of a data breach notification provision in PIPEDA (ETHI recommendations 23, 24 and 25). Such a provision is an important component of a comprehensive strategy to address the growing problem of identity theft. The Government proposes that the Privacy Commissioner be notified of any major breach of personal information, and that affected individuals and organizations be notified when there is a high risk of significant harm resulting from the breach. Ultimately, a requirement for data breach notification should encourage organizations to implement more effective security measures for the protection of personal information, while enabling consumers to better protect themselves from identity theft when a breach does occur. Industry Canada is seeking input in developing the parameters of a data breach notification provision, including, but not limited to, questions of timing, manner of notification, penalties for failure to notify, the need for a "without consent" power to notify credit bureaus, and appropriate "thresholds" for when organizations should be required to notify.
Industry Canada is also seeking further views on the issue of "work product" information (ETHI recommendation 2). The question of whether information created by individuals in their employment or professional capacity should be explicitly excluded from the definition of personal information has been a matter of significant debate. Industry Canada would therefore appreciate a wider range of views on whether an amendment to PIPEDA is needed, and, if so, how this should be implemented.
Furthermore, in order to ensure that PIPEDA is consistent with the needs of Canadian law enforcement agencies, the Government intends to clarify the meaning of lawful authority in PIPEDA as recommended by the Committee (ETHI recommendation 12). Industry Canada is seeking views and specific advice on how the concept of lawful authority could be better defined.
The Committee also recommended a number of issues for further consideration and/or consultation, including witness statements (ETHI recommendation 10), consent by minors (ETHI recommendation 15), and an assessment of the extent to which elements contained in the PIPEDA Awareness Raising Tools (PARTS) document may be set out in legislative form (ETHI recommendation 17). Industry Canada welcomes submissions on these matters.
Finally, Industry Canada is considering alternatives to the current process for the designation of investigative bodies (ETHI recommendation 6) and would appreciate any further views on this issue.
Submissions on the above, or on any other issues related to the government response that you may wish to raise, can be sent by email to PIPEDAconsultation@ic.gc.ca, by fax to 613-941-1164, or by mail to Richard Simpson, Director General, Industry Canada, Electronic Commerce Branch, 300 Slater Street, Ottawa, Ontario K1A 0C8.
The Government's response to the Fourth Report of the Standing Committee on Access to Information, Privacy and Ethics is available electronically on the World Wide Web at the following address: http://ic.gc.ca/specialreports.
For printed copies, please contact Publishing and Depository Services, Public Works and Government Services Canada, Ottawa, Ontario K1A 0S5; 1-800-635-7943 (Canada and U.S. toll-free telephone), 613-941-5995 (telephone), 1-800-465-7735 (TTY), 1-800-565-7757 (Canada and U.S. toll-free fax), 613-954-5779 (fax), publications@pwgsc.gc.ca (email), www. publications.gc.ca.
Labels: breach notification, identity theft, lawful access, lawful authority, pipeda review, privacy
Wednesday, September 12, 2007
Australian law reform commission calls for overhaul of country's privacy laws
The Australian Law Reform Commission has just released a hefty report calling for reforms to the country's privacy laws: ALRC Discussion Paper 72 Review of Privacy Laws - Contents.
Here's the media release accompanying the report:
ALRC - On-lineAustralian Law Reform Commission
Wednesday 12 September 2007
ALRC proposes overhaul of ‘complex and costly’ privacy laws
The Australian Law Reform Commission (ALRC) today released a blueprint with 301 proposals for overhauling Australia’s complex and costly privacy laws and practices.
Releasing Discussion Paper 72, Review of Australian Privacy Law, ALRC President Prof David Weisbrot said it was the product of the largest public consultation process in ALRC history: “We have received over 300 submissions and held over 170 meetings to date, including with business, consumers, young people, health officials, technology experts and privacy advocates and regulators.
“The clearest message from the community is that we must streamline our unnecessarily complex system. The federal Privacy Act sets out different principles for private organisations and for government agencies. On top of that, each state and territory has its own privacy laws or guidelines and some also have separate laws on health privacy.
“The ALRC is proposing there be a single set of privacy principles for information-handling across all sectors, and all levels of government. This will make it easier and less expensive for organisations to comply, and much more simple for people to understand their rights.
“The protection of personal information stored or processed overseas, as is now routine, is another serious concern. The ALRC wants to ensure that such information has at least the same level of protection as is provided domestically. We propose that a government agency or company that transfers personal information overseas without consent should remain accountable for any breach of privacy that occurs as a result of the transfer”, Prof Weisbrot said.
Commissioner in charge of the Inquiry, Prof Les McCrimmon, said that the ALRC also is proposing a new system of data breach notification: “There is currently no requirement to notify individuals when there has been unauthorised access to their information, such as when lists of credit card details are inadvertently published. Where there is a real risk of serious harm to individuals, we say they must be notified.”
Professor McCrimmon said that the ALRC also proposes the removal of the exemption for political parties from the Privacy Act. “Political parties and MPs should be required to take the same level of care when handling personal information as any other agency or organisation.”
Other key proposals include:
- introducing a new statutory cause of action where an individual’s reasonable expectation of privacy has been breached;
- abolishing the fee for ‘silent’ telephone numbers;
- expanding the enforcement powers of the Privacy Commissioner;
- imposing civil penalties for serious breaches of the Act; and
- introducing a more comprehensive system of credit reporting.
Review of Australian Privacy Law is available at no cost from the ALRC website, www.alrc.gov.au. The ALRC is seeking community feedback on these proposals before a final report and recommendations are completed in March 2008. Submissions close on 7 December 2007.
Thanks to Michel-Adrien Sheppard for the link: Library Boy: Review of Australian Privacy Law.
Labels: australia, breach notification, health information, privacy
Tuesday, September 04, 2007
Australian Commissioner fears breach notification could backfire
The Australian Privacy Commissioner is coming out against mandatory breach notification, which is a bit surprising given that the trends elsewhere are clearly in favour of notification. Just last week, the NZ Commissioner introduced breach notification guidelines.
Also of interest in this article is the fear over how pubs and bars use patrons' drivers license information:
Computerworld > 'Name-and-shame' disclosure could backfireAustralian federal privacy commissioner Karen Curtis is warning that calls for Australian companies to be subject to a compulsory name-and-shame data breach regime could backfire and create a compliance nightmare.
The statement is the strongest indication yet that a looming shake-up of the private sector provisions of the Privacy Act in Australia will not take the lead of US regulators, which have compelled corporations and government agencies to publish details of even minor infractions against customer data protection laws.
The warning comes as New Zealand organisations get to grips with our own Privacy Commissioner’s draft data breach disclosure guidelines, unveiled last week. Privacy Commissioner Marie Shroff has indicated she will consider whether breach guidelines should become a mandatory.
Curtis says serious consideration is being given to publicly identifying companies or agencies involved in incidents when there was a tangible risk of harm to consumers.
This is backed by research undertaken by her office over the past nine years that shows consumers favour pragmatism and common sense over onerous bureaucracy.
“The guts of it is that mandatory reporting for breaches should be examined, but you have to find the right threshold,” Curtis says. “We think there is merit, but not in all circumstances. Direct comparisons [with the US] are not ideal.”
...
Curtis says the ALRC review, which will make formal recommendations to Attorney-General Philip Ruddock next year, was needed because there was a mishmash of private, public, federal, state and local privacy regimes that sometimes acted to confuse people as to where they could go to seek advice and justice.
...
Curtis confirms her office is looking at a number of complaints about the alleged circulation of the personal details of pub patrons, who had been forced to provide identification that is electronically scanned and retained. Many licensed pubs and clubs now claim they are required to collect such information under liquor licensing laws. Curtis says she wants to know where the information collected from scans of drivers’ licences or other documents is going and how it is being used. Australia’s Office of the Privacy Commissioner was expected to release new guidelines for pubs last week and will warn establishments that have an annual turnover of more than A$3 million that they are subject to federal privacy protection laws. The pub ID problem has become a serious issue in Queensland. The state’s licensing authority, Queensland Transport, has started to remove addresses from drivers’ licences because they were being used by pub bouncers to find out where female patrons live.
Curtis says she intends to use Privacy Awareness Week, which started in Australia as in New Zealand last weekend, to emphasise the benefits that good privacy protections bring the community at large.
Labels: australia, breach notification, privacy
Sunday, August 26, 2007
NZ commissioner to release breach guidelines
New Zealand's privacy commissioner, Marie Shroff, is going to introduce voluntary privacy breach guidelines today. I understand they are modeled on those recenly produced by the Canadian Privacy Commissioner. I'll post a link when they are released.
Computerworld > Privacy Commissioner boosts breach disclosure drive with guidelinesPrivacy Commissioner Marie Shroff will today announce a draft guide for the management of data breaches in business and government, in what could be the first step towards introducing data breach disclosure laws to New Zealand.
The guidelines are not mandatory, however. Shroff says she may consider whether breach notification should be a mandatory part of New Zealand law, as is the case in parts of North America and has been recommended in Canada.
The guidelines say data breaches should be managed in four stages: containing and assessing the breach; evaluating the risks; considering or undertaking notification; and putting in place future prevention measures.
“Be sure to take each situation seriously and move immediately to investigate the potential breach,” the guidelines say. “Steps 1, 2 and 3 should be undertaken either simultaneously or in quick succession. Step 4 provides recommendations for longer-term solutions and prevention strategies. The decision on how to respond should be made on a case-by-case basis.”
UPDATE: Here are the materials posted on the NZ Commissioner's website:
Key steps for agencies responding to privacy breaches and privacy breach guidelines. The Commissioner welcomes feedback on the draft documents. Comments due by 28 September 2007.Download the documents
- Information paper DOC, 210KB
- Privacy Breach Guidance Material DOC, 258KB
- Privacy Breach Media Release DOC, 133KB
- Background Summary for the Media DOC, 140KB
Labels: breach notification, new zealand, privacy
Friday, August 03, 2007
Federal Privacy Commissioner releases privacy breach guidelines
The Federal Privacy Commissioner has just released privacy breach guidelines, which are similar to guidelines produced by the Ontario and British Columbia commissioners. Here is the press release, with links to the guidelines:
News Release: Privacy Commissioner releases privacy breach guidelines (August 1, 2007) - Privacy Commissioner of CanadaPrivacy Commissioner releases privacy breach guidelines
Ottawa, August 1, 2007 – New guidelines will help organizations take the right steps after a privacy breach, including notifying people at risk of harm after their information has been stolen, lost or mistakenly disclosed, says the Privacy Commissioner of Canada, Jennifer Stoddart.
The guidelines outline some of the key steps in responding to a breach, such as containing the breach, evaluating the risks associated with it, notifying the people affected and preventing future breaches.
“It’s clear that most businesses take seriously their responsibilities under Canada’s private-sector privacy law. I want to thank the industry groups, civil societies groups and privacy commissioners' offices that helped my office in developing these,” Commissioner Stoddart says.
The Office of the Privacy Commissioner (OPC) has become increasingly concerned about privacy breaches and breach notification following some major data breaches in recent months. Earlier this year, Commissioner Stoddart urged the federal government to amend the Personal Information Protection and Electronic Documents Act (PIPEDA) to make it mandatory for businesses to notify people when their personal information has been breached.
“Our new voluntary guidelines do not take away from the need for breach notification legislation,” the Commissioner says. “I would once again urge the Minister of Industry and his cabinet colleagues to help better protect Canadians by making breach notification a legal requirement for businesses.” The guidelines call on businesses to notify people that their personal information has been compromised in cases where the breach raises a risk of harm. For example, there may be a risk of identity theft or fraud in cases where sensitive personal information has been lost or stolen.
Organizations are also encouraged to inform the appropriate privacy commissioner(s) of a privacy breach. (In British Columbia, Alberta and Quebec, provincially regulated businesses should speak to their provincial privacy commissioners. In Ontario, breaches involving personal health information must be reported to the provincial commissioner.)
The OPC is currently investigating two high-profile privacy breach cases involving large amounts of personal information.
In one case, the Canadian Imperial Bank of Commerce reported to the OPC the disappearance of a hard drive containing the personal information and financial data of close to half a million clients of its subsidiary, Talvest Mutual Funds.
The other investigation, being conducted jointly with the Information and Privacy Commissioner of Alberta, is looking at a breach at TJX Companies Inc., which affected thousands of Canadians who shopped at TJX’s Winners and HomeSense stores.
The new guidelines as well as a privacy breach checklist and a list of organizations which participated in the consultation process to develop the guidelines are available on the OPC website, http://www.privcom.gc.ca/.
The Privacy Commissioner of Canada is mandated by Parliament to act as an ombudsman, advocate and guardian of privacy and the protection of personal information rights of Canadians.
Labels: alberta, bc, breach notification, british columbia, health information, identity theft, privacy, tjx
Monday, July 09, 2007
Few breaches lead to identity theft, GAO finds
Federal Computer Week recently ran an article on a new report from the GAO that found that few large privacy breaches lead to fraud. The report is here: Personal Information: Data Breaches Are Frequent, but Evidence of Resulting Identity Theft Is Limited; However, the Full Extent Is Unknown (Government Accountability Office); and the FCW.com article is here:
FCW.com News - Few breaches lead to identity theft, GAO findsAlthough data breaches in the public and private sectors are frequent, few incidents of identity theft have occurred as a result of the loss or unauthorized exposure of personal information, the Government Accountability Office said.
Fortunately for potential victims, only three of the 24 biggest breaches that GAO reviewed led to detected incidents of fraud on existing accounts and one incident of the unauthorized creation of a new account, according to GAO’s analysis of available data and interviews with researchers, law enforcement officials and industry representatives.
Retailers and a credit card processor were responsible for the data breaches that led to identity theft. GAO said it uncovered no clear evidence of fraud in 18 incidents, and insufficient data was available to make a determination in two incidents. However, it is difficult to know for certain the magnitude of identity theft, GAO said.
“The extent to which data breaches result in identity theft is not well-known, in large part because it can be difficult to determine the source of the data used to commit identity theft,” wrote David Wood, a director of GAO’s Financial Markets and Community Investment team, in a report posted today.
Perpetrators might hold stolen data for more than a year before using it to commit identity theft, law enforcement officials told GAO.
The data breaches GAO examined represent a fraction of the incidents in which public and private organizations have exposed or lost personal information. From 2005 through 2006, the news media have reported more than 570 data breaches. The House Oversight and Government Reform Committee identified more than 788 data breaches at 17 agencies from January 2003 through July 2006, and banks have reported several hundred incidents to their federal regulators in the past two years.
GAO studied breaches that were reported before July 2005. None involved federal agencies.
Encryption and hardware requirements for access control and certain data-reading equipment can prevent or restrict unauthorized access to data if it falls into the wrong hands.
Requirements to notify affected individuals could serve as incentives for organizations to improve data security practices so they can minimize legal liability and avoid the public relations issues that could result from a publicized breach. But that approach could also result in organizations spending money to develop incident response plans for identifying and notifying affected individuals.
A requirement that is too broad could result in notification of breaches that present little or no risk, perhaps leading consumers to disregard all notices, GAO said.
The agency instead recommended the use of a risk-based notification standard to identify the incidents in which the potential for harm exists and the appropriate actions to take. Consumers who are notified that their data was compromised could then take steps to protect themselves from possible identity theft, such as monitoring their bank or credit card statements for suspicious activity.
“Should Congress choose to enact a federal breach-notification requirement, use of the risk-based approaches that the federal banking regulators and the President’s Identity Theft Task Force advocate could avoid undue burden on organizations and unnecessary and counterproductive notifications to consumers,” Wood wrote in the report.
In April, the task force recommended a national notification standard for public and private organizations similar to its risk-based guidance for federal agencies. It involves notifying consumers who face a significant risk of identity theft, but it avoids excessive notification.
In addition, the Office of Management and Budget has issued guidance to help federal agencies respond to data breaches. No federal law requires that companies or other organizations notify affected individuals of data breaches, although federal banking regulators have provided guidance to the financial institutions they supervise and 36 states have enacted breach-notification laws.
Labels: breach notification, identity theft, privacy
Thursday, May 03, 2007
Parliamentary review of PIPEDA: Report
The Parliamentary Committee on Access to Information, Privacy and Ethics has just released its report following the five year PIEDA review:
ETHI (39-1) — Fourth Report: STATUTORY REVIEW OF THE PERSONAL INFORMATION PROTECTION AND ELECTRONIC DOCUMENTS ACT (PIPEDA) — Standing Committee on ACCESS TO INFORMATION, PRIVACY AND ETHICS - Committees of the House of CommonsThe Standing Committee onACCESS TO INFORMATION, PRIVACY AND ETHICS
has the honour to present its
Fourth Report
Pursuant to its mandate under Standing Order 108(2), the Committee has studied a Statutory Review of the Personal Information Protection and Electronic Documents Act (PIPEDA) and agreed to the following report:
The HTML version of this report will be available soon. In the meantime, the Committee is pleased to make available the report entitled STATUTORY REVIEW OF THE PERSONAL INFORMATION PROTECTION AND ELECTRONIC DOCUMENTS ACT (PIPEDA) (.PDF, 262 KB) in printable format.
Here are the recommendations:
47Recommendation 1
The Committee recommends that a definition of “business contact information” be added to PIPEDA, and that the definition and relevant restrictive provision found in the Alberta Personal Information Protection Act be considered for this purpose.
Recommendation 2
The Committee recommends that PIPEDA be amended to include a definition of “work product” that is explicitly recognized as not constituting personal information for the purposes of the Act. In formulating this definition, reference should be added to the definition of “work product information” in the British Columbia Personal Information Protection Act, the definition proposed to this Committee by IMS Canada, and the approach taken to professional information in Quebec’s An Act Respecting the Protection of Personal Information in the Private Sector.
Recommendation 3
The Committee recommends that a definition of “destruction” that would provide guidance to organizations on how to properly destroy both paper records and electronic media be added to PIPEDA.
Recommendation 4
The Committee recommends that PIPEDA be amended to clarify the form and adequacy of consent required by it, distinguishing between express, implied and deemed/opt-out consent. Reference should be made in this regard to the Alberta and British Columbia Personal Information Protection Acts.
Recommendation 5
The Committee recommends that the Quebec, Alberta and British Columbia private sector data protection legislation be considered for the purposes of developing and incorporating into PIPEDA an amendment to address the unique context experienced by federally regulated employers and employees.
Recommendation 6
The Committee recommends that PIPEDA be amended to replace the “investigative bodies” designation process with a definition of “investigation” similar to that found in the Alberta and British Columbia Personal Information Protection Acts thereby allowing for the collection, use and disclosure of personal information without consent for that purpose .
Recommendation 7
The Committee recommends that PIPEDA be amended to include a provision permitting organizations to collect, use and disclose personal information without consent, for the purposes of a business transaction. This amendment should be modeled on the Alberta Personal Information Protection Act in conjunction with enhancements recommended by the Privacy Commissioner of Canada.
Recommendation 8
The Committee recommends that an amendment to PIPEDA be considered to address the issue of principal-agent relationships. Reference to section 12(2) of the British Columbia Personal Information Protection Act should be made with respect to such an amendment.
Recommendation 9
The Committee recommends that PIPEDA be amended to create an exception to the consent requirement for information legally available to a party to a legal proceeding, in a manner similar to the provisions of the Alberta and British Columbia Personal Information Protection Acts.
Recommendation 10
The Committee recommends that the government consult with the Privacy Commissioner of Canada with respect to determining whether there is a need for further amendments to PIPEDA to address the issue of witness statements and the rights of persons whose personal information is contained therein.
Recommendation 11
The Committee recommends that PIPEDA be amended to add other individual, family or public interest exemptions in order to harmonize its approach with that taken by the Quebec, Alberta and British Columbia private sector data protection Acts.
Recommendation 12
The Committee recommends that consideration be given to clarifying what is meant by “lawful authority” in section 7(3)(c.1) of PIPEDA and that the opening paragraph of section 7(3) be amended to read as follows: “For the purpose of clause 4.3 of Schedule 1, and despite the note that accompanies that clause, an organization shall disclose personal information without the knowledge or consent of the individual but only if the disclosure is […]”
Recommendation 13
The Committee recommends that the term “government institution” in sections 7(3)(c.1) and (d) be clarified in PIPEDA to specify whether it is intended to encompass municipal, provincial, territorial, federal and non-Canadian entities.
Recommendation 14
The Committee recommends the removal of section 7(1)(e) from PIPEDA.
Recommendation 15
The Committee recommends that the government examine the issue of consent by minors with respect to the collection, use and disclosure of their personal information in a commercial context with a view to amendments to PIPEDA in this regard.
Recommendation 16
The Committee recommends that no amendments be made to PIPEDA with respect to transborder flows of personal information.
Recommendation 17
The Committee recommends that the government consult with members of the health care sector, as well as the Privacy Commissioner of Canada, to determine the extent to which elements contained in the PIPEDA Awareness Raising Tools document may be set out in legislative form.
Recommendation 18
The Committee recommends that the Federal Privacy Commissioner not be granted order-making powers at this time.
Recommendation 19
The Committee recommends that no amendment be made to section 20(2) of PIPEDA with respect to the Privacy Commissioner’s discretionary power to publicly name organizations in the public interest.
Recommendation 20
The Committee recommends that the Federal Privacy Commissioner be granted the authority under PIPEDA to share personal information and cooperate in investigations of mutual interest with provincial counterparts that do not have substantially similar private sector legislation, as well as international data protection authorities.
Recommendation 21
The Committee recommends that any extra-jurisdictional information sharing, particularly to the United States, be adequately protected from disclosure to a foreign court or other government authority for purposes other than those for which it was shared.
Recommendation 22
The Committee recommends that PIPEDA be amended to permit the Privacy Commissioner to apply to the Federal Court for an expedited review of a claim of solicitor-client privilege in respect of the denial of access to personal information (section 9(3)(a)) where the Commissioner has sought, and been denied, production of the information in the course of an investigation.
Recommendation 23
The Committee recommends that PIPEDA be amended to include a breach notification provision requiring organizations to report certain defined breaches of their personal information holdings to the Privacy Commissioner.
Recommendation 24
The Committee recommends that upon being notified of a breach of an organization’s personal information holdings, the Privacy Commissioner shall make a determination as to whether or not affected individuals and others should be notified and if so, in what manner.
Recommendation 25
The Committee recommends that in determining the specifics of an appropriate notification model for PIPEDA, consideration should be given to questions of timing, manner of notification, penalties for failure to notify, and the need for a “without consent” power to notify credit bureaus in order to help protect consumers from identity theft and fraud.
Labels: alberta, bc, breach notification, british columbia, health information, identity theft, lawful authority, pipa, pipeda review, privacy
Wednesday, May 02, 2007
Alberta order on consent and withdrawal thereof
Order P2007-003Two Complainants brought complaints under the Personal Information Protection Act with respect to the collection, use and disclosure of their personal information by International Stereo Ltd., (now operating as Urban Audio Video Inc.) (the “Retailer”). The information had been collected by the Retailer and then conveyed to Wells Fargo Financial Corporation of Canada, so as to permit the latter organization to conduct credit checks for determining whether it would grant credit for buying the Retailer’s merchandise. Although the Complainants signed applications containing clauses consenting to use of personal information for credit checks, they said they had been assured their personal information would not be used in this way. They also said they had been led to believe the cards for which they applied would allow them to get 10% discounts on purchases. As well, one of them complained that his request to withdraw his application had been refused.
The Adjudicator found that the Retailer collected, used and disclosed the Complainants’ personal information in violation of section 7 of the Act (collection, use and disclosure without consent), that it failed to provide adequate notification of the purpose for collection in contravention of section 13, and that it failed to cease collecting, using or disclosing the personal information after consent had been withdrawn, in violation of section 9(4).
Labels: alberta, breach notification, pipa, privacy, retail
Thursday, March 15, 2007
Dion pledges breach notification if he's elected PM
Stephane Dion, the leader of the Liberal Party of Canada, pledged in a speech yesterday to require breach notification if he becomes Prime Minister. He also pledged to implement the recommendations of the federal Anti-Spam Task Force:
Liberal.ca :: Speeches:Protecting Our Homes and Our Rights March 14, 2007
...
- To protect Canadian seniors, we will act on the recommendations of the Privacy Commissioner to address the problem of identity theft. There were almost 8,000 reports of identity theft in the past year, resulting in more than $16 million being lost, much of it taken from vulnerable seniors. A lifetime of hard work and savings can vanish in an instant. We need tougher laws to prevent this kind of crime.
- One of the main recommendations of the Privacy Commission is that we need to change private-sector privacy laws, so companies are forced to notify customers when their personal information gets leaked. If your social security number gets into the wrong hands, you deserve to find out about it, so you can avoid becoming a victim of identity theft. This kind of change would finally cause businesses to take the security of their customers more seriously.
- Another recommendation is that we need laws implementing the recommendations of the federal Task Force on Spam – recommendations that have so far been ignored by the Conservatives. Spam is the weapon of choice for identity thieves, who use phony e-mails to trick people into revealing personal information. Canada is the only G-8 country without anti-spam legislation, and a Liberal government led by me will change that.
Thanks to Michael Geist for pointing me to Dion's speech.
PS: I'm not sure why the first point is solely for the protection of seniors.
Labels: breach notification, identity theft, privacy
Saturday, March 10, 2007
Hospitals must encrypt patient data on portable devices
The Information and Privacy Commissioner of Ontario yesterday released order HO-004 under the Personal Health Information Protection Act following the theft of a laptop containing confidential personal health information on 2,900 patients at the Sick Kids hospital in Toronto.
The order requires the hospital
- to develop or revise and implement policies and procedures the ensure that records of personal health information are safeguarded
- to develop a corporate policy that prohibits the removal of identifiable personal health information in from the premises. If identifiable personal health information must be removed in electronic form, it must be encrypted;
- to develop an encryption policy for mobile computing devices, a policy relating to the use of virtual private networks, a privacy breach policy, and to educate staff regarding the policies how to secure the information contained on mobile computing devices.
While the order directly relates to a hospital, it would applyl to all health information custodians in the province of Ontario and will likely serve as guidance to all health care providers in the country.
For more info, see TheStar.com - News - Sick Kids ordered to encrypt all electronic patient files.
Labels: breach notification, health information, laptop, ontario, phipa, privacy
Saturday, February 24, 2007
Commissioner pressured bank to go public on data loss
Labels: breach notification, privacy
Sunday, February 04, 2007
Consumer response and responsibility
Dissent, at the Chronicles of Dissent (part of Pogowasright) asks whether consumer stupidity plays a role in privacy breaches and the response. Dissent points to an article from my local newspaper, the Chronicle Herald, quoted below.
I can't say that Canadians are more prudent or insistent about their privacy than our cousins below the border, or more stupid. In my experience on the east coast of Canada, most folks around here are much more trusting of the companies they do business with. The cynicism from down south hasn't quite permeated this neck of the woods. One thing we generally are more tolerant of is government regulation, such as that governing privacy.
We have not yet seen any provinces or the federal government come up with mandatory breach notification, with the narrow exception contained in Ontario's health privacy law. In that regard, we are lagging behind most of the states in the US.
Winners reassures CanadiansSecurity breach did not involve cards issued north of border, says retailer
By AMANDA-MARIE QUINTINO The Canadian Press
TORONTO — Assurances from Winners and HomeSense that a security breach reported last month did not involve Canadian debit-card transactions isn’t making much of dent with customers of the two retail chains.
Not much can keep them from their bargain hunting.
The deals to be found at Winners makes the risk of becoming the victim of credit card fraud worthwhile, said Sherry Croney as she slowly sifted through the blouse racks at one of the chain’s cavernous stores in downtown Toronto.
Croney said she never uses her credit card when clothes shopping, and even if she did, a security breach wouldn’t stop her.
...
"Our computer security experts have now completed their investigation of the portion of our computer network that handles Winners and HomeSense transactions, and they have advised us that they do not believe that debit cards issued by Canadian banks were compromised in the intrusion," said a TJX statement posted on the Winners website.
I note there is only a reference to Canadian debit cards.... nothing said about credit cards.
Labels: breach notification, privacy, retail, tjx
Friday, February 02, 2007
PIPEDA Hearings - Days 9 and 10
The PIPEDA Review Hearings have resumed after a recess and Michael Geist continues to link to notes taken at the hearings (see: Michael Geist - PIPEDA Hearings - Days 9 (banking industry) and 10 (Chamber of Commerce, Insurance)). The focus has shifted to discussions of breach notification, a topic that now seems to have strong support on the committee.
Labels: breach notification, pipeda review, privacy
Saturday, January 27, 2007
Will this be beginning of breach notification in Canada?
The recent personal information breaches in Canada have prompted a lot of discussion about breach notification.
This may be the upswell of citizen concern that will prompt legislative change in Canada. From today's Halifax Chronicle Herald:
The ChronicleHerald.ca - Should retailers come clean? Businesses not obligated to alert consumers when information is stolenBy CLARE MELLOR Business Reporter
Retailers and financial institutions in Canada don’t have to tell customers when thieves have stolen their personal information.
Recent cases of data theft at Winners and the loss of a hard drive at CIBC have made headlines across the country, alerting Canadian consumers to be on guard for identity theft, but these security breaches could be the tip of the iceberg, privacy experts say.
"There are probably a whole lot more incidents out there that we haven’t heard about because the businesses have no legal reason that requires them to tell the consumers involved," Halifax lawyer David Fraser, a privacy specialist, said Friday.
"One of the big questions on law reform in this area is whether a business should have a duty to notify people whose information has been compromised."
CIBC, which was earlier taken to task by federal privacy commissioner Jennifer Stoddart for lapses in security involving misdirected faxes, issued a news release and sent letters to Talvest mutual-fund holders last week. The company said a backup computer file containing their personal information had gone missing in transit.
TJX Cos., American operator of Winners and HomeSense, recently revealed that computer hackers had broken into its system, but the firm has not said how many customers had personal data stolen.
About 30 states have laws requiring businesses to notify their customers when their personal information has been stolen or lost, Mr. Fraser said.
A parliamentary committee has been reviewing Canada’s federal privacy law. Requirements to notify the public when a breach happens are being discussed.
When Ms. Stoddart appears before the committee, she will likely call for changes to the law requiring businesses to inform consumers when their information has been stolen or gone missing, Anne-Marie Hayden, spokeswoman for the privacy commissioner’s office, said Friday.
Under Canada’s privacy law, businesses and banks must keep personal information secure and not share it without client consent.
While Ms. Stoddart’s office can’t fine or penalize businesses that repeatedly break the law, it can pursue legal action through the Federal Court, Ms. Hayden said.
"It would be safe to say that most of the time when the commissioner makes recommendations (to tighten privacy practices), those changes are implemented," she said .
But David Malamed, a forensic accountant, said it is clear many companies are not taking their privacy obligations seriously enough.
"A lot of the reason that it is happening is that the focus for a lot of companies is on the bottom line," said Mr. Malamed, who works at Grant Thornton in Toronto
"As systems advance, people get smarter and the question is how money is being invested into protecting these systems. . . . There are different methods that you can go about to protect your customer information that will help prevent this from happening or at least reduce it to a greater degree."
There have been media reports of fraudulent purchases made with customer information stolen from Winners.
A Canadian law firm, Merchant Law Group, which has offices in Saskatchewan and Alberta, has already launched a class-action suit over the security breach.
But there is some question about whether Canadian consumers can successfully sue for theft or mishandling of their personal information, Mr. Fraser said.
"If you are the subject of fraud, you may be able to successfully sue them," he said. "But if you can’t prove harm, it is much more difficult."
(cmellor@herald.ca)
Labels: alberta, breach notification, identity theft, pipeda review, privacy, tjx
Thursday, January 25, 2007
Privacy breaches and notification in Canada
Yesterday's weekly Globe & Mail law page had a good article on issues related to breach notification in Canada. It quotes three privacy lawyers with whom I've had the pleasure of serving on the CBA Privacy Section executive: David Young of Lang Michener, Michael Power of Gowlings and John Beardwood of Faskens. See: globeandmail.com: Privacy breaches.
Labels: breach notification, privacy
Monday, January 22, 2007
A call for Canadian breach notification
Michael Geist's latest Law Bytes column in the Toronto Star presses the case for mandatory breach notification in the wake of the recent TJX and CIBC privacy breaches. See: Michael Geist - Privacy Breaches Expose Flaws in Law.
Labels: breach notification, privacy, tjx
Sunday, January 21, 2007
Litany of small scale privacy breaches
Last week, Global Television's main news program has aired a number of reports relating to privacy breaches at Canada Revenue Agency. This has led to a number of viewers contacting the TV network to report their own versions, involving Revenue Canada and others.
The Global Maritimes ran a report on Thursday about a woman in Nova Scotia who was repeatedly sent the credit card information, including the "secret code" for a cardholder in Ontario. When she informed them of the screw-up, they told her she was wrong and kept resending the info to her. When contacted by Global's reporter, the Ontario cardholder was furious that he had no idea that a woman in Bridgewater, Nova Scotia, could have gone to town on his Visa account and the company apparently never did anything to protect his account.
There are also a number of small scale breaches recounted as comments to the CRA breach story on the Global TV website:
Taxman moves to protect privacy
- in 1988 while living in Woodstock ON, I received an other pe... Wanda
- It happened to me last month. I received information that be... vivian
- Revenue Canada provides the Quebec Govt with income informat... Yves
- I thought maybe I should share my incident although I had ... Sherri
- This is not quite the same but equally disturbing. My husba... Margaret
- Last year I went to the post office to pick up my passport a... Elaine
- How about receiving mail from the government addressed Maureen
- Summer, 2005 I requested a Revenue Canada summary and receiv... Frank
- My dad's Disability Tax credit approval notice was enclosed ... Marnie
Labels: breach notification, incident, privacy
Wednesday, January 17, 2007
Taxman moves to protect privacy
I was interviewed today for Global National's most recent report on privacy problems at the Canada Revenue Agency (our IRS, for my American readers). Since earlier reports on misdirected tax information, many more people have come out to report they have also been the unwitting recipients of information about other taxpayers. See: Taxman moves to protect privacy and also note the many comments in which others relate receiving others' personal information.
I think you can get the video of the feature here: http://video.canada.com/VideoContent.aspx?13750&vc=1&popup=1, but it seems hit and miss to me.
Labels: breach notification, cra, media-mention, privacy, privacy act, public sector, vanity
Wednesday, January 10, 2007
CIPPIC calls for mandatory privacy breach notification
The Canadian Internet Policy and Public Interest Clinic has released a whitepaper calling for manadatory breach notification. Speficially, CIPPIC is calling for an amendment to PIPEDA:
Amend Principle 7 of PIPEDA to include a requirement to notify affected individuals of a security breach that results in the acquisition of unencrypted personal information by an unauthorized person. Such requirement should include specifics regarding the type of personal information and breach that triggers the obligation to notify, form and content of notices, timing of notices, who should be notified, etc. Failure to notify affected individuals as required under the Act should be subject to tough penalties.Notification should be required when designated personal information has been, or is reasonably believed to have been, acquired by an unauthorized person. Good faith acquisition of personal information by an employee or agent of the agency for the purposes of the agency should not trigger the notification requirement, provided that the personal information is not used or subject to further unauthorized disclosure.
An "unauthorized person" means:
a) A person who is not an employee or agent of the person that maintains the designated personal information;b) An employee or an agent of the person that maintains the designated personal information who
(i) exceeds his or her authority to access the designated personal information; or(ii) uses the information for purposes not related to his or her duties.
"Designated personal information" is information, in electronic or paper form, which includes the first name, initial, or middle name, and last name, or address, in combination with any of the following data: government issued identification number including social insurance number, driver’s license number, or health card number; account numbers, credit or debit card numbers, or other unique identifiers issued by other organizations together with any security code, password or access code that would permit access to the individual's information. Information that is encrypted, redacted, or otherwise altered by any method or technology in such a manner that the name or data elements are unreadable by unauthorized persons does not constitute "designated personal information".
Labels: breach notification, health information, privacy
Thursday, December 21, 2006
CBA Says Deficiencies in PIPEDA Must Be Addressed in Five-Year Review
This was posted on the CBA site a while ago, but I'm working through a backlog of links after a really busy few months ...
Among those testifying at the PIPEDA review was Brian Bowman, Chair of the Privacy and Access Law Section of the CBA, who presented recommendations on behalf of the CBA. Michael Geist's site has a summary of the testimony presented on behalf of the CBA, but the release below links to the written submission:
CBA Says Deficiencies in PIPEDA Must Be Addressed in Five-Year ReviewOTTAWA – The Canadian Bar Association says there are deficiencies in the Personal Information Protection and Electronic Documents Act (PIPEDA) that must be amended so the law addresses both individual privacy rights and organizations’ needs to collect and use information appropriately.
“It is essential that we be vigilant in respecting the balance of interests in the collection and use of personal information. We must oppose unnecessary erosions of privacy by both government and non-governmental organizations,” says Brian Bowman of Winnipeg, Chair of the CBA’s National Privacy and Access Law Section.
The CBA submission criticizes four key areas of the law:
- PIPEDA and litigation. Exceptions in PIPEDA relating to litigation are too narrow and impede well-established procedures. The CBA recommends the law should be neutral in regard to the litigation process.
- Enforcement. The CBA says enforcement should be more effective, but continue to reflect principles of fundamental justice. The CBA recommends an effective enforcement mechanism, such as an impartial tribunal, that would operate informally and have the power to make orders and award damages.
- Notification of breaches. The CBA says notification of breaches of privacy should be balanced in approach. The CBA recommends that individuals be notified of a breach only when mechanisms like encryption have failed, or when the information is personal and sensitive.
- Trans-border information flow. The CBA says information transferred across borders must be protected according to Canadian law. The CBA recommends that where personal information is being stored or processed outside Canada, additional protections – such as contracts – be required to add to the security of that information.
“We believe our suggestions will provide assistance in amending PIPEDA to address deficiencies and concerns that have become apparent since the law was enacted,” says Brian Bowman. “This five-year review of the legislation provides an excellent opportunity to re-assess that balance.”
Brian Bowman will present the CBA submission to the Access to Information, Privacy and Ethics Committee on Monday, Dec. 11, 2006 at 3:30 p.m. in Room 371, West Block. The submission is available on the CBA website at:http://www.cba.org/CBA/submissions/pdf/06-58-eng.pdf
The Canadian Bar Association is dedicated to improvement in the law and the administration of justice. Some 37,000 lawyers, law teachers, and law students from across Canada are members.
- 30 -
CONTACT: Hannah Bernstein, Canadian Bar Association, Tel: (613) 237-2925, ext. 146; E-mail: hannahb@cba.org.
(Full disclosure: I was on the committee that developed the recommendations.)
Labels: breach notification, cba, pipeda review, privacy
Tuesday, December 19, 2006
Notification coming to Ontario public sector privacy laws?
Thanks to John Gregory for passing this along ...
Bill 152 has now passed in the Ontario Legislature and is heading for royal assent. This Bill contains a number of amendments to a range of statutes, but most interestingly provides for the creation of regulations for notifications if information is disclosed contrary to the Freedom of Information and Protection of Privacy Act (and its equivalent that applies to municipalities):
9. Subsection 60 (1) of the Act is amended by adding the following clauses:(b.1) requiring the head of an institution to assist persons with disabilities in making requests for access under subsection 24 (1) or 48 (1);. . . . .
(d.1) providing for procedures to be followed by an institution if personal information is disclosed in contravention of this Act;
. . . . .
(f.1) respecting the disposal of personal information under subsection 40 (4), including providing for different procedures for the disposal of personal information based on the sensitivity of the personal information;
It'll be interesting to see what the regs look like.
Labels: breach notification, ontario, privacy, public sector
Monday, December 11, 2006
Breach notification assessment tool
B.C.: Key Steps in Responding to Privacy Breaches (http://www.oipc.bc.ca)Ontario:
What to do if a privacy breach occurs: Guidelines for government organizations, (http://www.ipc.on.ca/images/Resources/up-prbreach.pdf)
What to do When Faced With a Privacy Breach: Guidelines for the Health Sector, (http://www.ipc.on.ca/images/Resources/up-hprivbreach.pdf)
Labels: bc, breach notification, british columbia, health information, privacy
Friday, December 01, 2006
CIPPIC calls for major changes to PIPEDA
Again on the topic of the PIPEDA review, the Canadian Internet Policy and Public Interest Clinic (CIPPIC) has released its written submission to the Parliamentary Committee on Ethics, Access to Information and Privacy. Not surprisingly, they are calling for some major changes:
We therefore propose a number of amendments designed to clarify rights and obligations, to close gaps, and to give the regime the "teeth" it is clearly lacking. Such amendments include:
- giving the Commissioner (or an associated Tribunal) order-making powers;
- reducing barriers to the enforcement of PIPEDA rights via Federal Court;
- permitting class actions under PIPEDA;
- providing for punitive as well as compensatory damages in court;
- mandatory naming of respondents in published Commissioner findings;
- mandatory Commissioner reporting on complaints;
- expanding the list of offences under PIPEDA;
- removing the "reasonable grounds" requirement for audits; and
- giving the Commissioner powers to share information with her counterparts.
While PIPEDA's redress and enforcement regime is most need of reform, some important substantive provisions of the Act suffer from lack of clarity, and others leave strange gaps. We have therefore proposed amendments to clarify and add provisions dealing with:
- the criteria for valid consent;
- data breach notification;
- reasonable limits on collection, use and disclosure;
- children's privacy;
- openness and individual access;
- attempted collection, use and disclosure;
- state surveillance; and
- the definition of "organization".
Update (20070118): For links to the full hearing transcripts, go to: Canadian Privacy Law Blog: PIPEDA Review Transcripts.
Labels: breach notification, pipeda review, privacy, surveillance
Day four of the PIPEDA hearings
Michael Giest has a summary of the fourth day of testimony before the Parliamentary Committee conducting the PIPEDA review hearings:
Michael Geist - PIPEDA Hearings - Day 04 (B.C. Privacy Commissioner Loukidelis and Professor Val Steeves):"Wednesday's PIPEDA hearing featured B.C. Privacy Commissioner David Loukidelis and University of Ottawa professor Val Steeves. Commissioner Loukidelis went even further than the federal privacy commissioner in downplaying significant change. Loukidelis downplayed his order making power (a last resort), security breach notification (more evidence on impact needed), and even the concerns associated with cross-border transfers to the U.S. (can always pick a different private sector company). Professor Steeves highlighted the privacy challenges posed by new technologies and offered some specific reform recommendations. Natalie Senst was in attendance on Wednesday afternoon and she filed the following report:..."
Update (20070118): For links to the full hearing transcripts, go to: Canadian Privacy Law Blog: PIPEDA Review Transcripts.
Labels: breach notification, british columbia, pipeda review, privacy
Tuesday, November 28, 2006
Commissioner speaks at the PIPEDA review hearings
Michael Geist has a summary of the third day of the PIPEDA review hearings, at which the Privacy Commissioner appeared. She called for mandatory breach notification and amendments to PIPEDA to get around the recent Blood Tribe that curtailed her ability to review claims of privilege. Check it out: Michael Geist - PIPEDA Hearings - Day 03 (Privacy Commissioner of Canada).
Update (20070118): For links to the full hearing transcripts, go to: Canadian Privacy Law Blog: PIPEDA Review Transcripts.
Labels: breach notification, pipeda review, privacy
Thursday, October 12, 2006
British group tests "tagging" of air passengers
BBC News, via Boing Boing! is reporting that a British research instutite is field testing a new surveillance system at an airport in Hungary. The system combines RFID and video surveillance to track people throughout the airport. There are two wrinkles to be worked out: (i) making sure that passengers can't remove or swap their tags and (ii) those pesky things called "civil liberties". Hmm. Might I be so bold as to suggest (i) tracking collars and (ii) saying that only evildoers need worry about civil liberties?
BBC NEWS Technology Air passengers 'could be tagged':Electronically tagging passengers at airports could help the fight against terrorism, scientists have said.
The prototype technology is to be tested at an airport in Hungary, and could, if successful, become a reality "in two years".
The work is being carried out at a new research centre, based at University College London, set up to find technological solutions to crime.
Other projects include scanners for explosives and dirty bomb radiation.
Dr Paul Brennan, an electrical engineer, is leading the tagging project, known as Optag.
He said: "The basic idea is that airports could be fitted with a network of combined panoramic cameras and RFID (radio frequency ID) tag readers, which would monitor the movements of people around the various terminal buildings."
The plan, he said, would be for each passenger to be issued with a tag at check-in.
He said: "In our system, the location can be detected to an accuracy of 1m, and video and tag data could be merged to give a powerful surveillance capability."
Civil liberties
The tags do not store any data, but emit a signal containing a unique ID which could be cross-referenced with passenger identification information. In the future, added Dr Brennan, this could incorporate biometric data.
The project still needs to overcome some hurdles, such as finding a way of ensuring the tags cannot be switched between passengers or removed without notification.
The issue of infringement of civil liberties will also be key.
But potentially, said Dr Brennan, the tags could aid security by allowing airports to track the movement patterns of passengers deemed to be suspicious and prevent them from entering restricted areas.
It could also aid airports by helping evacuation in case of a fire, rapidly locating children, and finding passengers who are late to arrive at the gate.
The "proof of concept" of the system is about to be tested at Debrecen airport in Hungary. If successful, claimed Dr Brennan, it could be available elsewhere within two years.
The new centre will also be investigating a range of other airport security tools.
Labels: air travel, airlines, breach notification, privacy, rfid, surveillance, video surveillance
![]()

The Canadian Privacy Law Blog is licensed under a
Creative Commons Attribution-Noncommercial-No Derivative Works 2.5 Canada License.