The Canadian Privacy Law Blog: Developments in privacy law and writings of a Canadian privacy lawyer, containing information related to the Personal Information Protection and Electronic Documents Act (aka PIPEDA) and other Canadian and international laws.
Recent Posts
- This blog has moved
- Some thoughts on street photography
- RCMP changes rules for criminal records checks
- Saskatchewan amends privacy regs to permit solicia...
- US Federal judge declares warrantless wiretapping ...
- Commisser releases discussion paper on cloud compu...
- Heathrow worker given police warning for body scan...
- How Privacy Vanishes Online, a Bit at a Time
- Facebook plans to allow users to "share" location
- Drawing the curtain on ISP cooperation with law en...
On Twitter
About this page and the author
 The author of this blog,
David T.S. Fraser, is a Canadian privacy lawyer who practices with the
firm of McInnes Cooper. He is the author of the Physicians' Privacy Manual. He has a national and international practice advising corporations and individuals on matters related to Canadian privacy laws.
The author of this blog,
David T.S. Fraser, is a Canadian privacy lawyer who practices with the
firm of McInnes Cooper. He is the author of the Physicians' Privacy Manual. He has a national and international practice advising corporations and individuals on matters related to Canadian privacy laws.
For full contact information and a brief bio, please see David's profile.
Please note that I am only able to provide legal advice to clients. I am not able to provide free legal advice. Any unsolicited information sent to David Fraser cannot be considered to be solicitor-client privileged.
Privacy Calendar
Archives
- January 2004
- February 2004
- March 2004
- April 2004
- May 2004
- June 2004
- July 2004
- August 2004
- September 2004
- October 2004
- November 2004
- December 2004
- January 2005
- February 2005
- March 2005
- April 2005
- May 2005
- June 2005
- July 2005
- August 2005
- September 2005
- October 2005
- November 2005
- December 2005
- January 2006
- February 2006
- March 2006
- April 2006
- May 2006
- June 2006
- July 2006
- August 2006
- September 2006
- October 2006
- November 2006
- December 2006
- January 2007
- February 2007
- March 2007
- April 2007
- May 2007
- June 2007
- July 2007
- August 2007
- September 2007
- October 2007
- November 2007
- December 2007
- January 2008
- February 2008
- March 2008
- April 2008
- May 2008
- June 2008
- July 2008
- August 2008
- September 2008
- October 2008
- November 2008
- December 2008
- January 2009
- February 2009
- March 2009
- April 2009
- May 2009
- June 2009
- July 2009
- August 2009
- September 2009
- October 2009
- November 2009
- December 2009
- January 2010
- February 2010
- March 2010
- April 2010
Links


Blogs I Follow
Small Print
The views expressed herein are solely the author's and should not be attributed to his employer or clients. Any postings on legal issues are provided as a public service, and do not constitute solicitation or provision of legal advice. The author makes no claims, promises or guarantees about the accuracy, completeness, or adequacy of the information contained herein or linked to. Nothing herein should be used as a substitute for the advice of competent counsel.
This web site is presented for informational purposes only. These materials do not constitute legal advice and do not create a solicitor-client relationship between you and David T.S. Fraser. If you are seeking specific advice related to Canadian privacy law or PIPEDA, contact the author, David T.S. Fraser.
Thursday, March 29, 2007
Supreme Court to hear PIPEDA appeal
For past coverage, see: Canadian Privacy Law Blog: Commissioner cannot compel privileged documents: FCA.
This will be an important case, both for PIPEDA and for the ability of non-court tribunals to evaluate claims of privilege.
Labels: privacy
TJX: At least 45.7M card numbers stolen
Sorry for the light blogging for the last little while. Busy times at work, two family weddings and March break for the kids intervened. But I'm back.
The Associated Press is reporting that TJX has disclosed that their recent breach compromised 45.7 million credit and debit card numbers (including mine). The breach went on for eighteen months and the card information the company had on file dated as far back as December 2002. See: TJX: At least 45.7M card numbers stolen - Yahoo! News.
Thursday, March 22, 2007
Alberta Commissioner upholds cameras in locker rooms at health club
This is likely to spur some interesting discussion:
OIPCA complaint was made against the Organization which operates the “Talisman Centre for Sport and Wellness”. The Complainant stated that the Organization had placed overt security cameras in the Talisman Centre’s men’s locker rooms. The Complainant was concerned about a loss of privacy and that patrons of the Centre would be unable to change without being viewed by the cameras. The Organization stated that the security cameras were installed in 1997 in response to over 900 incidents of theft and property damage during the years 1994-97. The security cameras were installed after all other means to prevent criminal activity had failed. The cameras’ field of vision was restricted to the lockers and had no zoom, panoramic or audio capabilities. The cameras were not actively monitored and a protocol was in place which restricted the viewing of images to instances where there was an incident or reported criminal activity with a case number assigned by the Calgary Police Service. Viewing of the images occurs only in the presence of two senior staff members or by one such member and a police constable. If images are not reviewed they are automatically overwritten in approximately 21 days. After installation of the cameras there was a sharp reduction in criminal activity. As of the date of the Organization’s submission to the Commissioner only 19 images had ever been viewed. The Commissioner found that due to the history of theft, the attempt to use other measures prior to using security cameras as a last resort, and the fact that the images recorded were only accessed in the event of a criminal incident, that the Organization’s collection of personal information was for purposes that were reasonable, as required by section 11(1) of the Personal Information Protection Act (“PIPA”). However, the Organization’s signage was not in compliance with section 13(1) of PIPA. The Commissioner ordered the Organization to change the signage.
Click to view more information Order P2006-008
Labels: alberta, health information, pipa, privacy
Wednesday, March 21, 2007
FBI confirms contracts with telcos for providing customer info
FBI Confirms Contracts with AT&T, Verizon and MCI
The FBI's general counsel, Valerie Caproni, testified today on Capitol Hill that the FBI entered into contracts with AT&T, Verizon and MCI to harvest phone records on American citizens under a national security letter program that has come under fire from Congress and the Justice Department's Office of Inspector General for circumventing privacy laws.
Caproni confirmed during a House Judiciary hearing that AT&T and Verizon, which bought MCI in 2005, had and continue to have contracts with the FBI that compensate phone companies for turning over the toll records of customers connected to counterterroism investigations. The telecoms entered into the contracts in May 2003, according to the report issued last week by the DoJ Inspector General.
"The contract essentially pays for the man hours or the personnel cost for the people who have to do the work," said FBI Assistant Director John Miller in an interview with Wired News last night. "We want dedicated people who handle our requests or do nothing else."
Labels: law enforcement, privacy
Saturday, March 17, 2007
Equifax and Privacy Commissioner settle spat over audit
In August 2006, the Privacy Commissioner of Canada initiated an audit of Equifax under PIPEDA, which requires reasonable grounds to believe the audited company is in breach of the law. Equifax sought judicial review of that decision, arguing that the Commissioner did not have the grounds to initiate an audit. The parties have now settled the judicial review proceeding and it appears the audit is close to being concluded.
CNW TelbecPrivacy Commissioner works with Equifax to conclude audit
OTTAWA, March 16 /CNW Telbec/ - The Office of the Privacy Commissioner of Canada announced today that it has successfully negotiated a resolution with regard to litigation involving its audit of the credit reporting agency, Equifax.
The Commissioner's Office launched an audit of Equifax in August 2006 under the Personal Information Protection and Electronic Documents Act (PIPEDA), Canada's private sector privacy law. The intention was to audit the personal information management practices of Equifax and, more specifically, its online identification and authentication system. The Office has since published guidelines for businesses on identification and authentication, which are available on its web site.
Under section 18(1) of PIPEDA, the Commissioner may audit the personal information management practices of an organization if she has reasonable grounds to believe that the organization is contravening a provision of the Act.
Equifax had launched an application for judicial review, challenging whether the Privacy Commissioner's Office had reasonable grounds to conduct the audit in the first place. The two parties recently negotiated a resolution, the details of which are in the court documents. A notice of discontinuance and minutes of settlement were filed with the Federal Court on March 14, 2007.
"I am pleased that Equifax agreed to discontinue their court challenge because it is important for us to make use of all the tools at our disposal, including exercising our powers to audit personal information management practices in the private sector," said Jennifer Stoddart, Privacy Commissioner of Canada. "Ultimately, what we determine in our work can only be of benefit to the organizations involved and their customers."
Throughout the course of the litigation, the Office's audit of Equifax remained ongoing and a report will be provided to the credit reporting agency.
The Office of the Privacy Commissioner of Canada is mandated by Parliament to act as an ombudsman, advocate and guardian of the privacy and protection of personal information rights of Canadians.
Labels: privacy
Friday, March 16, 2007
FTC investigating TJX, Winners parent company
This really shouldn't be a big surprise:
FTC Launches Investigation Of T.J. Maxx Parent Company - Yahoo! NewsThe U.S. Federal Trade Commission Tuesday confirmed that it has launched an investigation of TJX, the parent company of T.J. Maxx, Marshalls, HomeGoods, and other stores. While the FTC wouldn't reveal the nature of the investigation or when it began, it's likely the result of a large data breach that allowed cyberintruders to steal customer data.
Should TJX be worried? During the past few years, ChoicePoint showed everyone just how much power the FTC wields. That company wound up paying $10 million in civil penalties and $5 million in customer redress after it handed over consumers' names, addresses, Social Security numbers, and credit reports to fraudsters working out of Los Angeles County. But the monetary penalty is just the beginning, says Jo Anne Adlerstein, an attorney with Thelen Reid Brown Raysman & Steiner LLP. ChoicePoint also had to implement a new IT security system, and their security systems will be audited every two years for the next 20 years. If TJX is found to be in violation of privacy laws, "it will be the beginning of an ongoing relationship with the FTC," she says.
The FTC's investigation of TJX should put all companies that handle customer data on notice. "Companies must think in terms of, 'What if the FTC stops by to see me tomorrow? What will they find?'" Adlerstein says....
Thursday, March 15, 2007
Dion pledges breach notification if he's elected PM
Stephane Dion, the leader of the Liberal Party of Canada, pledged in a speech yesterday to require breach notification if he becomes Prime Minister. He also pledged to implement the recommendations of the federal Anti-Spam Task Force:
Liberal.ca :: Speeches:Protecting Our Homes and Our Rights March 14, 2007
...
- To protect Canadian seniors, we will act on the recommendations of the Privacy Commissioner to address the problem of identity theft. There were almost 8,000 reports of identity theft in the past year, resulting in more than $16 million being lost, much of it taken from vulnerable seniors. A lifetime of hard work and savings can vanish in an instant. We need tougher laws to prevent this kind of crime.
- One of the main recommendations of the Privacy Commission is that we need to change private-sector privacy laws, so companies are forced to notify customers when their personal information gets leaked. If your social security number gets into the wrong hands, you deserve to find out about it, so you can avoid becoming a victim of identity theft. This kind of change would finally cause businesses to take the security of their customers more seriously.
- Another recommendation is that we need laws implementing the recommendations of the federal Task Force on Spam – recommendations that have so far been ignored by the Conservatives. Spam is the weapon of choice for identity thieves, who use phony e-mails to trick people into revealing personal information. Canada is the only G-8 country without anti-spam legislation, and a Liberal government led by me will change that.
Thanks to Michael Geist for pointing me to Dion's speech.
PS: I'm not sure why the first point is solely for the protection of seniors.
Labels: breach notification, identity theft, privacy
Saved searches provide the smoking gun in muder case
Speaking of Google and privacy, here's an interesting story. The data came from the computer of the accused, but ...
Welcome to www.dailyrecord.com - Updates - Cop: Wife googled 'How to commit murder':"At exactly 5:45:34 on April 18, 2004 a computer taken from the office of the attorney of Melanie McGuire, did a search on the words 'How To Commit Murder.'
That same day searches on Google and MSN search engines, were conducted on such topics as `instant poisons,` `undetectable poisons,' 'fatal digoxin doses,' and gun laws in New Jersey and Pennsylvania.
Ten days later, according to allegations by the state of New Jersey, McGuire murdered her husband, William T. McGuire, at their Woodbridge apartment, using a gun obtained in Pennsylvania, one day after obtaining a prescription for a sedative known as the 'date rape' drug...."
Librarians to talk about Patriot Act challenge in Vermont
Seven Days, the Vermont alternative web weekly is running a preview of a presentation to be given by Peter Chase and George Christian later this month. Both are librarians who were on the receiving end of national security letters under the USA Patriot Act and fought them with the assistance of the ACLU.
If I get my hands on the presentation materials, I'll post them here.Seven Days: Librarians, No Longer Gagged, Detail Patriot Act AbusesWINDSOR, CT — In September 2003, then-U.S. Attorney General John Ashcroft ridiculed the American Library Association for its “breathless reports and baseless hysteria” about a USA PATRIOT Act provision that allows FBI agents to search library records without a warrant. Until he left office in early 2005, Ashcroft repeatedly denied that the feds were snooping into Americans’ reading habits and computer activities.
In July 2005, Peter Chase and George Christian discovered firsthand that Ashcroft was lying. They couldn’t tell anyone, though — not friends, co-workers or family members — even as Congress debated the Patriot Act’s reauthorization.
Christian is executive director of the Library Connection, a nonprofit consortium in Windsor, Connecticut. Chase is president of the group’s executive committee and director of one of its 27 member libraries. An eight-month gag order prevented them from disclosing that they’d received a “national security letter” from the FBI seeking confidential library computer records.
“We were shocked,” Chase recalls. “None of us had ever heard of a national security letter before.”
....
Chase and Christian, along with fellow committee members Barbara Bailey and Janet Nocek, decided to fight the warrantless search. Though the librarians were never told why the FBI wanted their files, a federal prosecutor later disclosed that it was a matter of “domestic surveillance.”
The Connecticut librarians have since been released from their gag order. On March 20, they’ll speak at the University of Vermont about how they fought the Patriot Act — and won. Civil libertarians say their case is a chilling example of the threats to privacy rights in the post-9/11 era.
“My initial twinge in opposing [the FBI] was that I was aiding and abetting a catastrophe,” recalls Christian. “But right away, I could glean that they weren’t worried that someone was going to cause a catastrophic event tomorrow.” The letter, he notes, was dated two months earlier, and the records the FBI wanted were six months old. In Connecticut, as in 47 other states, library records are protected by law.
Vermont’s own protections for library records aren’t as strong as those in other states, notes Trina Magi, who chairs Vermont’s Intellectual Freedom Committee. Though library records are exempt from the open-records law, she says, nothing explicitly prevents librarians from disclosing them. Moreover, last year’s Patriot Act reauthorization did nothing to alleviate librarians’ concerns.
“What people read at libraries is confidential,” Chase argues. “People should feel free to come to the library and look up whatever information they need, without thinking that Big Brother is looking over their shoulder.”
In August 2005, the Connecticut librarians sued the federal government, with help from the ACLU. Initially, they were collectively known as “John Doe.” However, because of sloppy redacting of court records by government attorneys, Christian’s and Chase’s identities were made public, and reporters soon came calling.
...
Even after the librarians’ names were known, the gag order still barred them from discussing their case. Those restrictions reached absurd proportions. When the government asserted that the librarians’ presence in federal court in Bridgeport raised a “national security issue,” they had to watch the proceedings on closed-circuit TV from a locked courtroom in Hartford. When an appeal was heard in federal court in Manhattan, the librarians were allowed to attend but were prohibited from entering the courtroom together, sitting together, speaking to each other, or making eye contact with their attorneys.
Tellingly, the librarians were released from the document request and gag order shortly after the Patriot Act was reauthorized in March 2006. Once the government dropped its appeal, the librarians lost their legal standing to challenge the statute’s constitutionality.
Today, Christian is troubled by how many Americans have apparently complied with NSL requests. “I’m trying to figure out in my mind how 30,000 NSLs can be issued each year,” he says, “and in five years only two people have said, ‘I don’t think so.’”
Peter Chase and George Christian give a lecture titled "Gagged by the Government: Two Librarians Tell How They Resisted the USA PATRIOT Act." Tuesday, March 20, 3:30-5 p.m. Bailey Howe Library, University of Vermont. Free. Info, 656-5723.
Labels: law enforcement, libraries, national security, patriot act, privacy, surveillance
Wednesday, March 14, 2007
Google to anonymize older data
This is an interesting development, though some think it is too late and doesn't go far enough:
Official Google Blog: Taking steps to further improve our privacy practices3/14/2007 03:00:00 PM
Posted by Peter Fleischer, Privacy Counsel-Europe, and Nicole Wong, Deputy General Counsel
When you search on Google, we collect information about your search, such as the query itself, IP addresses and cookie details. Previously, we kept this data for as long as it was useful. Today we're pleased to report a change in our privacy policy: Unless we're legally required to retain log data for longer, we will anonymize our server logs after a limited period of time. When we implement this policy change in the coming months, we will continue to keep server log data (so that we can improve Google's services and protect them from security and other abuses)—but will make this data much more anonymous, so that it can no longer be identified with individual users, after 18-24 months.
Just as we continuously work to improve our products, we also work toward having the best privacy practices for our users. This includes designing privacy protections into our products (like Google Talk's “off the record” feature or Google Desktop’s “pause” and “lock search” controls). This also means providing clear, easy to understand privacy policies that help you make informed decisions about using our services.
After talking with leading privacy stakeholders in Europe and the U.S., we're pleased to be taking this important step toward protecting your privacy. By anonymizing our server logs after 18-24 months, we think we’re striking the right balance between two goals: continuing to improve Google’s services for you, while providing more transparency and certainty about our retention practices. In the future, it's possible that data retention laws will obligate us to retain logs for longer periods. Of course, you can always choose to have us retain this data for more personalized services like Search History. But that's up to you.
Our engineers are already busy working out the technical details, and we hope to implement this new data policy over the coming months (and within a year's time). We’ll communicate more as we work out these details, but for now, we wanted you to know that we’re working on this additional step to strengthen your privacy.
If you want to know more, read the log retention FAQ (PDF).
There's more here: WIRED Blogs: 27B Stroke 6: Google To Anonymize Data -- Updated. And here: Google adopts tougher privacy measures.
Thanks to Boing Boing for the tipoff.
Tuesday, March 13, 2007
Canadians leery of releasing personal census information
Today, Statistics Canada released the first findings from the 2006 census. This was the first year that respondents were asked whether they would consent to have their personally-identifiable information released far in the future. The Canadian Press is reporting that fewer than six in ten Canadians agreed that their information could be made public after 2098. Interesting ... (See: TheStar.com - News - Canadians leery of releasing personal data.)
Labels: privacy
Sunday, March 11, 2007
Economics of identity theft
Stephen Dubner and Steven Levitt, the authors of the best-selling book Freakonomics and the consistently interesting Freakonomics Blog have a very interesting piece in today's New York Times on the economics of identity theft and credit card fraud: Identity Theft - Identity Crisis - Stephen J. Dubner and Steven D. Levitt - New York Times. Read more at the blog: Freakonomics Blog » Who Cares About Identity Theft?
Labels: fraud, identity theft, privacy
Saturday, March 10, 2007
UK Information Commissioner calls for international harmonization
Richard Thomas, the Information Commissioner of the UK is calling for international privacy standards, particularly focusing on the ongoing squabbles between Europe and the United States. (See: UK official calls for international privacy standards.).
I agree that harmonization should be a goal, but I am concerned that this may lead to a "lowest common denominator" system which would reduce the protection that some jurisdictions afford to their citizens' privacy. The following quote suggests this may be the outcome:
"There could be 'scope for less bureaucracy, less emphasis on prior authorization and a more concrete focus on preventing real harm', he said."
"Privacy" is not just about preventing fraud and indentity theft. Most modern privacy regimes are about giving people choices about how (and whether) their information is collected, used and disclosed. Reducing emphasis on "prior authorization" would likely undermine this.
Canada's PIPEDA, for all its faults, has shown that you can have a comprehensive privacy law that is based on consent and still permits legitimate business use of personal information.
Hospitals must encrypt patient data on portable devices
The Information and Privacy Commissioner of Ontario yesterday released order HO-004 under the Personal Health Information Protection Act following the theft of a laptop containing confidential personal health information on 2,900 patients at the Sick Kids hospital in Toronto.
The order requires the hospital
- to develop or revise and implement policies and procedures the ensure that records of personal health information are safeguarded
- to develop a corporate policy that prohibits the removal of identifiable personal health information in from the premises. If identifiable personal health information must be removed in electronic form, it must be encrypted;
- to develop an encryption policy for mobile computing devices, a policy relating to the use of virtual private networks, a privacy breach policy, and to educate staff regarding the policies how to secure the information contained on mobile computing devices.
While the order directly relates to a hospital, it would applyl to all health information custodians in the province of Ontario and will likely serve as guidance to all health care providers in the country.
For more info, see TheStar.com - News - Sick Kids ordered to encrypt all electronic patient files.
Labels: breach notification, health information, laptop, ontario, phipa, privacy
Friday, March 09, 2007
US DOJ audit discloses abuses of National Security Letter powers
This probably isn't a big surprise to a lot of people, but I'm surprised to see it publicly disclosed:
Mueller Admits Fault in FBI IntrusionsMar 9, 8:33 PM EST
By LARA JAKES JORDAN
Associated Press Writer
WASHINGTON (AP) -- The nation's top two law enforcement officials acknowledged Friday the FBI broke the law to secretly pry out personal information about Americans. They apologized and vowed to prevent further illegal intrusions.
Attorney General Alberto Gonzales left open the possibility of pursuing criminal charges against FBI agents or lawyers who improperly used the USA Patriot Act in pursuit of suspected terrorists and spies.
The FBI's transgressions were spelled out in a damning 126-page audit by Justice Department Inspector General Glenn A. Fine. He found that agents sometimes demanded personal data on people without official authorization, and in other cases improperly obtained telephone records in non-emergency circumstances.
The audit also concluded that the FBI for three years underreported to Congress how often it used national security letters to ask businesses to turn over customer data. The letters are administrative subpoenas that do not require a judge's approval.
"People have to believe in what we say," Gonzales said. "And so I think this was very upsetting to me. And it's frustrating."
"We have some work to do to reassure members of Congress and the American people that we are serious about being responsible in the exercise of these authorities," he said.
Under the Patriot Act, the national security letters give the FBI authority to demand that telephone companies, Internet service providers, banks, credit bureaus and other businesses produce personal records about their customers or subscribers. About three-fourths of the letters issued between 2003 and 2005 involved counterterror cases, with the rest for espionage investigations, the audit reported.
...
FBI Director Robert S. Mueller said many of the problems were being fixed, including by building a better internal data collection system and training employees on the limits of their authority. The FBI has also scrapped the use of "exigent letters," which were used to gather information without the signed permission of an authorized official.
...
The American Civil Liberties Union said the audit proves Congress must amend the Patriot Act to require judicial approval anytime the FBI wants access to sensitive personal information.
...
Both Gonzales and Mueller called the national security letters vital tools in pursuing terrorists and spies in the United States. "They are the bread and butter of our investigations," Mueller said.
...
In 2000, for example, the FBI issued an estimated 8,500 requests. That number peaked in 2004 with 56,000. Overall, the FBI reported issuing 143,074 requests in national security letters between 2003 and 2005.
But that did not include an additional 8,850 requests that were never recorded in the FBI's database, the audit found. A sample review of 77 case files at four FBI field offices showed that agents had underreported the number of national security letter requests by about 22 percent.
Additionally, the audit found, the FBI identified 26 possible violations in its use of the letters, including failing to get proper authorization, making improper requests under the law and unauthorized collection of telephone or Internet e-mail records.
The FBI also used exigent letters to quickly get information - sometimes in non-emergency situations - without going through proper channels. In at least 700 cases, these letters were sent to three telephone companies to get billing records and subscriber information, the audit found.
On the Net:
The report is at: http://www.usdoj.gov/oig/reports/FBI/index.htm
Justice Department: http://www.usdoj.gov
FBI: http://www.fbi.gov
Labels: law enforcement, national security, patriot act, privacy, warrants
Privacy, customer information and law enforcement
I had the honour of being asked to give a presentation for today's Dalhousie Student Association for Law and Technology conference. I spoke on the topic of privacy, customer information and law enforcement (200k PDF).
I was on a panel with a federal prosecutor and was surprised that we were in substantial agreement on the relationship between private businesses and law enforcement.
The rest of the day was great, as it included such heavyweights in IT law as Rod Burgar, Don Johnston, Duncan Card, Sunny Handa.
Labels: law enforcement, presentations, privacy, warrants
Monday, March 05, 2007
NHLPA investigated for allegedly reviewing members' e-mail
The Toronto Police are apparently investigating whether the National Hockey League Players' Association reviewed or blocked e-mail of members provided through the NHLPA's website. The police report has been referred to crown prosecutors, who will determine whether charges should be laid.
TheStar.com - News - Email furor has NHL players on edgeToronto police are investigating complaints that executives at the NHL Players Association accessed and in some cases blocked the email accounts of players who have challenged the hiring of the union's executive director.
The allegations by players is the latest salvo in the battle for control of the splintered Toronto-based union.
Last month, the players voted for an independent investigation into the hiring of NHLPA executive director Ted Saskin in July 2005.
The investigation is also looking into the circumstances that led to the players association accepting a labour contract that included for the first time a cap on player salaries.
For the past two weeks, police have been looking into whether Saskin and Ken Kim, the union's senior director of business, ordered technical support staff at the union to access player email accounts hosted by the union, and whether such an action would be illegal, four sources familiar with the investigation told the Star.
Toronto police have now presented their findings to a Crown counsel, who will decide whether there is enough evidence to lay criminal charges....
Labels: privacy, surveillance
Saturday, March 03, 2007
Canada.com pawns off webmail service to US provider; says PIPEDA no longer applies
Apparently, CanWestGlobalAsperOmniMedia has outsourced the Canada.com e-mail service to an American company, Velocity Services, Inc.
This is the blurb from the Canada.com website:
About canada.comWhere will my canada.com e-mail account information be stored?
canada.com e-mail (the "Service") is provided by Velocity Services, Inc. ("VSI"), a company located in and conducting its business from the United States. By registering for and/or logging on to the Service, you accept and acknowledge that the information processed or stored outside of Canada may be available to the foreign government of the country in which the information or the entity controlling it, is situated under a lawful order made in that jurisdiction and no longer falls under the jurisdiction of Canada's Personal Information Protection and Electronic Documents Act ("PIPEDA") nor be subject to canada.com's Privacy Statement.
That's all well and good, but I'm pretty confident that you can't wave a magic wand and say that PIPEDA no longer applies. Either of two things have happened here: (a) VSI is providing this service on behalf of CanWest, or (b) CanWest has now sold Canada.com's e-mail service to VSI. In neither case would PIPEDA cease to apply. For Canadian customers, there is enough of a real and substantial connection between the service and Canada for Canadian laws to apply. This would include PIPEDA.
In this conclusion, I have some comfort in the recent decision in Lawson v. Accusearch Inc., 2007 FC 125 (CanLII):
"[49] We revert to geographical considerations, and the concept of forum non conveniens. The collection and communication of private information was both here (Canada) and there (United States) (Libman v. The Queen, 1985 CanLII 51 (S.C.C.), [1985] 2 S.C.R. 178). The location of the website and the jurisdiction in which Accusearch Inc. was incorporated are not all controlling.[50] It would not be appropriate to comment further on the discretion, if any, of the Commissioner to decline to exercise the jurisdiction given her by Parliament. The decision before me was that Parliament had not given her jurisdiction. However, I raise this point of discretion because it may be relevant when this matter is referred back to her for further investigation, or in other complaints. We do not know the status of the complaint filed in the United States, or the risk of double jeopardy to the respondent.
[51] In conclusion, PIPEDA gives the Privacy Commissioner jurisdiction to investigate complaints relating to the transborder flow of personal information."
Thanks to Canadian Journalist :: Canada.com now ...AMERICAN??? for the link. Time to cancel my old Canada.com e-mail account.
Labels: privacy
Friday, March 02, 2007
Prison sentence for installing spyware in the UK
A UK court has sentenced a 67 year old man to four months in prison for consipring to install spyware on the compuer of the accused's estranged wife, whom he suspected was hiding assets. See: DP thinker: First UK case on Spyware.
Labels: europe, privacy, spyware, surveillance, uk
US Appeals Court upholds eight year sentence for theft of e-mail addresses
According to Computerworld, a US Appeals Court has upheld the eight year setence for the theft of billions of e-mail addresses from Acxiom: Appeals court: Stiff prison sentence in Acxiom data theft case stands. It's worth noting that the convictions were under the federal hacking staute and not theft of information simpliciter.
Thursday, March 01, 2007
This time it's personal
In addition to my weekly New Yorker magazine, today's mail contained a plain envelope with a PO Box return address. From a mile away, I could tell it was a credit card. Like many people recently, my bank has sent me a new credit card in the mail because I shopped at Winners. According to the letter, there is reason to believe my credit card was compromised in the Winners/TJX breach. The form letter tells me that there's been no evidence of fraudulent activity, but this is just in case.

When the TJX story broke, I attempted to contact their privacy officer through the address on the website. What I was looking for was a fax number becuase I did not want to communicate with them, particularly about my credit card, via e-mail. That was months ago and no contact and no reply. Not impressive.
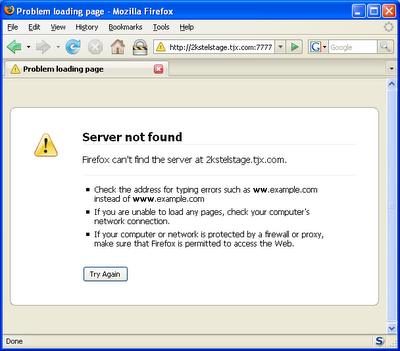
I just went to the Winners website and tried to check out their IMPORTANT CUSTOMER ALERT, which connects (or rather doesn't connect) to a TJX server:
Less impressive.
Going directly to the TJX website provided a working link:
As TJX’s President and Chief Executive Officer, I want our customers to know how much I personally regret any difficulties you may experience as a result of the unauthorized intrusion into our computer systems. We are working with leading computer security firms to investigate the problem and enhance our computer security in order to protect our customers’ data. We are dedicating significant resources to evaluate the issue. Given the nature of the breach, the size and international scope of our operations and the complexity of the way credit card transactions are processed, the evaluation is, by necessity, taking time.Since we learned of the probability of a breach in mid-December 2006, we have cooperated with law enforcement as well as with the banks and credit card companies that process our customer transactions. Further, we have established customer helplines in three countries and are making available a great deal of helpful information on our company websites.
We are committed to continue to address the situation and to provide periodic updates as we learn more. We have reported updated information in a press release which you will find below.
Additionally, I encourage you to access the information we are providing on this website to learn more about steps you can take to protect your credit and debit card information, or to contact our special customer helplines.
With the help of computer security experts, we have strengthened the security of our computer systems and we believe customers should feel safe shopping in our stores. We value the trust our customers place in us and again, I’d like you to know that we sincerely apologize for any difficulties you may be caused. Thank you for continuing to shop at our stores and for your years of loyal patronage.
Respectfully,
Carol Meyrowitz
President and Chief Executive Officer
Those affected may seek some perverse comfort that TJX may face significant penalties under the PCI Data Security Standard.
It will be interesting (but certainly not remedial in any way) to see what the Privacy Commissioner concludes about this investigation.
Labels: cardsystems, privacy, tjx
![]()

The Canadian Privacy Law Blog is licensed under a
Creative Commons Attribution-Noncommercial-No Derivative Works 2.5 Canada License.